Using HashiCorp Vault with Terraform
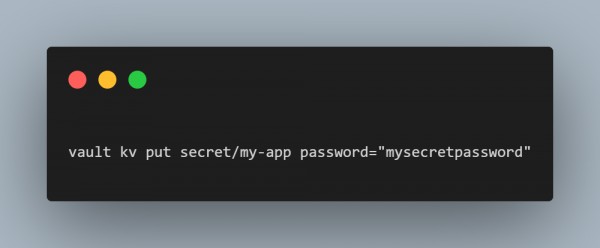
Store a Secret in Vault:
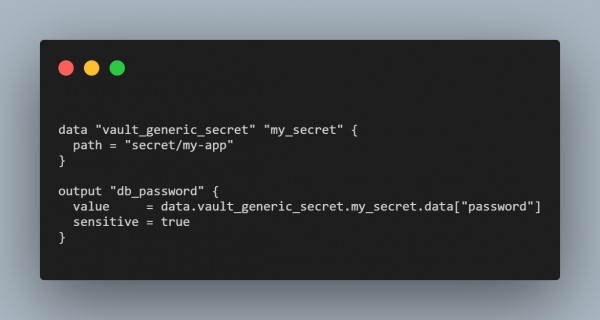
Vault Provider Setup in Terraform:

Retrieve and Use the Secret:
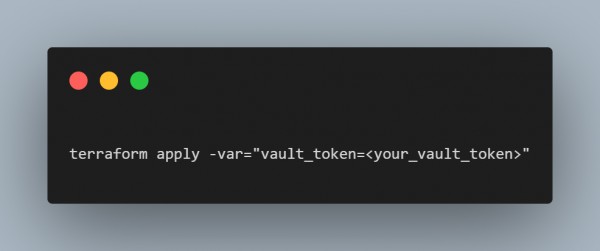
Run Terraform:
Using AWS Secrets Manager with Terraform
Store the Secret in AWS Secrets Manager:

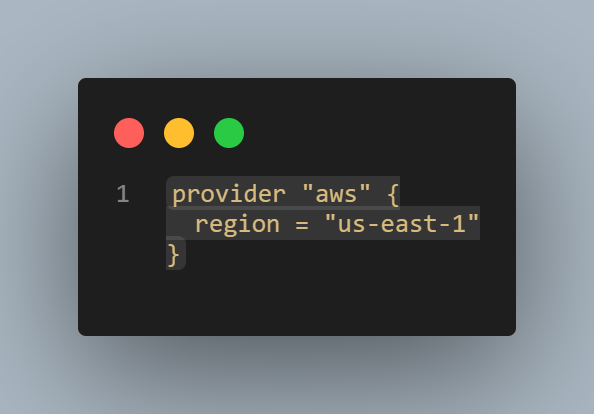
AWS Provider Setup:
Retrieve and Use the Secret:

Security Best Practices
Hard Code Secrets: Never directly put the secret into Terraform files.
Sensitive Flag: Use the sensitive flag to hide outputs by setting it to true.
Secure State: State files to be stored securely using S3 with encryption.
This ensures that secrets handling by Terraform is secured.
 REGISTER FOR FREE WEBINAR
X
REGISTER FOR FREE WEBINAR
X
 Thank you for registering
Join Edureka Meetup community for 100+ Free Webinars each month
JOIN MEETUP GROUP
Thank you for registering
Join Edureka Meetup community for 100+ Free Webinars each month
JOIN MEETUP GROUP