One of the most important components to handle within security contexts for DevOps workflows is the management of secrets such as API keys, passwords, or other forms of credentials. Here are some best practices and coding techniques useful for effective secrets management:
-
Use a dedicated secrets management tool: Use a dedicated secrets management tool: HashiCorp Vault, AWS Secrets Manager, and Azure Key Vault are designed to securely store and manage access to sensitive data. These tools integrate seamlessly with CI/CD pipelines and offer features like encryption, strict access controls, and audit logging to safeguard your secrets.
-
Sensitive data should never be stored in environment variables in plaintext. Instead, use a reference to a secure location, such as a path to a secrets management tool like Vault, to ensure proper protection and access control.
-
Non-Sensitive Data Environment Variables: Environment variables are good for non-sensitive configuration data. Sensitive data should never be stored as plaintext in environment variables. Instead, it should be referenced through a secure location, such as a path to a vault like HashiCorp Vault, to ensure safe handling and access control.
-
Configuration Management: Use data bags or vaults encrypted in tools like Ansible, Puppet, or Chef. In this way, one can keep the information encrypted at rest and decrypt only when being used, thus not exposing it to potential exposure.
Also, apply the best practices: Rotating secrets on a regular basis is included with expiry times. However, this automatically reduces many risks. Rotate from your secrets management tool and through code updates, these secrets across systems and applications.
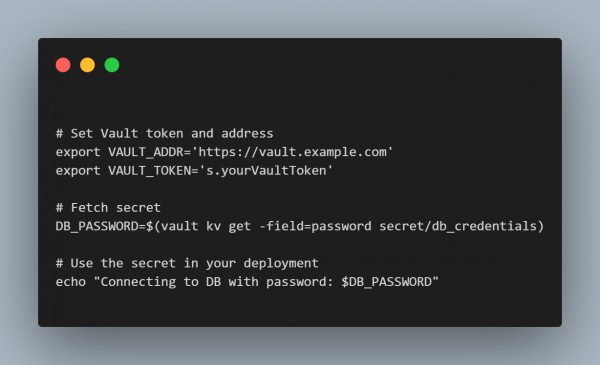
By including a secrets management tool and following these best practices, you will secure all of your DevOps processes against unauthorized access.
If you're looking for a better career, I personally suggest you take the DevOps Post Graduate Program!
 REGISTER FOR FREE WEBINAR
X
REGISTER FOR FREE WEBINAR
X
 Thank you for registering
Join Edureka Meetup community for 100+ Free Webinars each month
JOIN MEETUP GROUP
Thank you for registering
Join Edureka Meetup community for 100+ Free Webinars each month
JOIN MEETUP GROUP