Cyber Security and Ethical Hacking Internship ...
- 15k Enrolled Learners
- Weekend/Weekday
- Live Class
In this digital age, it is very important to make sure that networks and systems can still be accessed. But attackers are always testing these limits with Denial of Service attacks, which are attempts to overload systems and slow them down or shut them down completely.
This blog goes into detail about what DoS attacks are, how they work, the different types of them, famous cases from history, and the ways you can protect your network.
Denial-of-Service attacks are planned attempts to stop or slow down a computer, service, or network by sending a lot of fake requests to it. Attackers make systems slow, unresponsive, or completely unavailable by taking advantage of their limited bandwidth, processing power, or memory. It rarely lead to data theft, but they can do a lot of damage to a company’s finances and image. Attackers use a variety of methods, such as sending badly formatted files or taking advantage of software flaws. Sometimes, they even use botnets to make their attacks stronger.
At its core, it floods a target with too much data or requests for resources. It is possible to make this barrage by:
Real-time traffic analysis and anomaly detection are important for finding these strange trends so that quick steps can be taken to fix them.
A DoS attack only comes from one source, but a Distributed Denial of Service attack targets a person by using multiple compromised systems. The distributed nature of DDoS gives attackers a number of benefits, including:
It attacks come in many ways, and each one takes advantage of a different weakness. Let’s look at these common types:
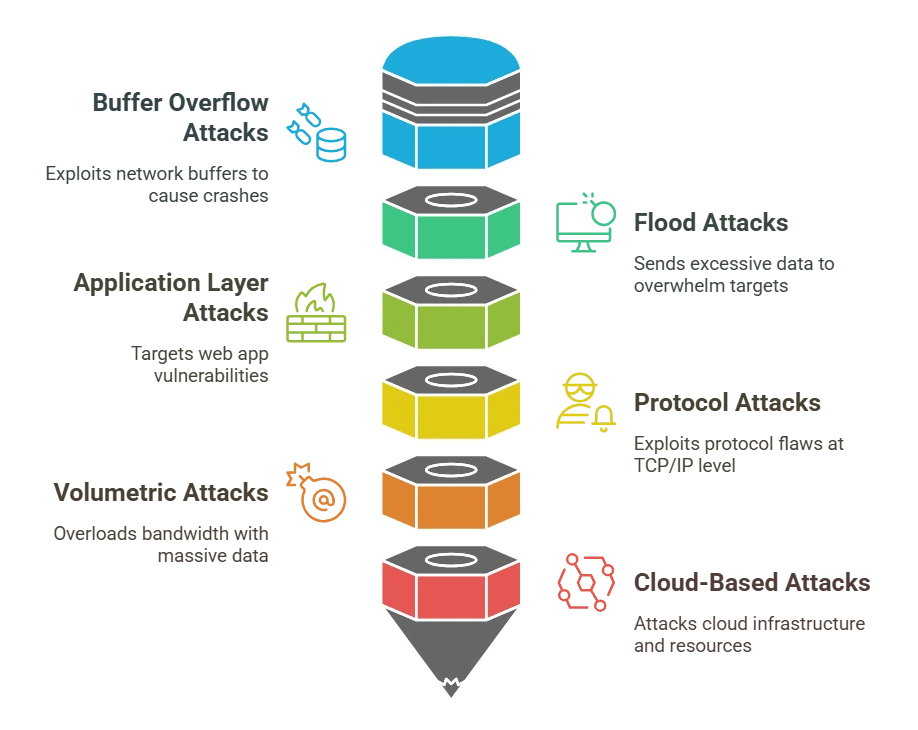 Buffer Overflow Attacks
Buffer Overflow AttacksAn attacker initiates a buffer overflow attack when they want to send excess data to a network buffer than it can handle. This can lead to system crashes or strange behavior. This category includes:
To fix the problem, people usually use strict input validation, regular system changes, and more complex security features like DEP and ASLR.
Flood attacks send a lot of data to a target all at once. Attacks like the 2016 Dyn attack, which utilized a lot of network resources, are common. Rate limiting, proactive traffic tracking, and using firewalls and content delivery networks (CDNs) are all good ways to stop this.
These attacks are aimed at specific web apps and look for weak spots in login pages, search functions, or database queries. Attacks like HTTP floods and Slowloris can use up all of an application’s resources. These can be stopped by web application firewalls (WAFs), code optimization, and strict patch management for businesses.
Protocol attacks use flaws in network protocols, mostly at the TCP/IP level, to do damage. Some examples are
As a defense, you can use SYN cookies, set up firewalls, and keep your network hardware up to date.
Volumetric attacks try to overwhelm the network’s bandwidth by sending a lot of data at once, usually through botnets. UDP and ICMP floods are examples of tactics that can overwhelm even the strongest systems. Most of the time, scrubbing centers, strong traffic filtering, and adaptive rate limits are needed to stop these attacks.
Attacks using DoS are not impossible in the cloud. Cloud systems are often attacked by going after the hypervisor or using crypto-jacking to take over resources. Some of these are:
As a defense, you can protect the hypervisor, separate the virtual machines, and constantly monitor the resources.
DDOS Attack Explained
History has a number of important cases that show how threats are changing:
Traffic filtering, intrusion detection systems, and overall cybersecurity defenses have all gotten better because of these events.
Reflecting on past incidents sets the stage for understanding the signs of an ongoing attack.Next, let’s see how to identify if a system is under assault.
Signs of a DoS attack include:
To tell the difference between a real surge and an attack, you need monitoring tools and real-time analytics that work well.
Recognizing the signs is crucial; now, let’s explore the tools and methods attackers use to launch these assaults.
Starting with the basics, let’s delve into how Botnets and Malware play a central role in DoS attacks.
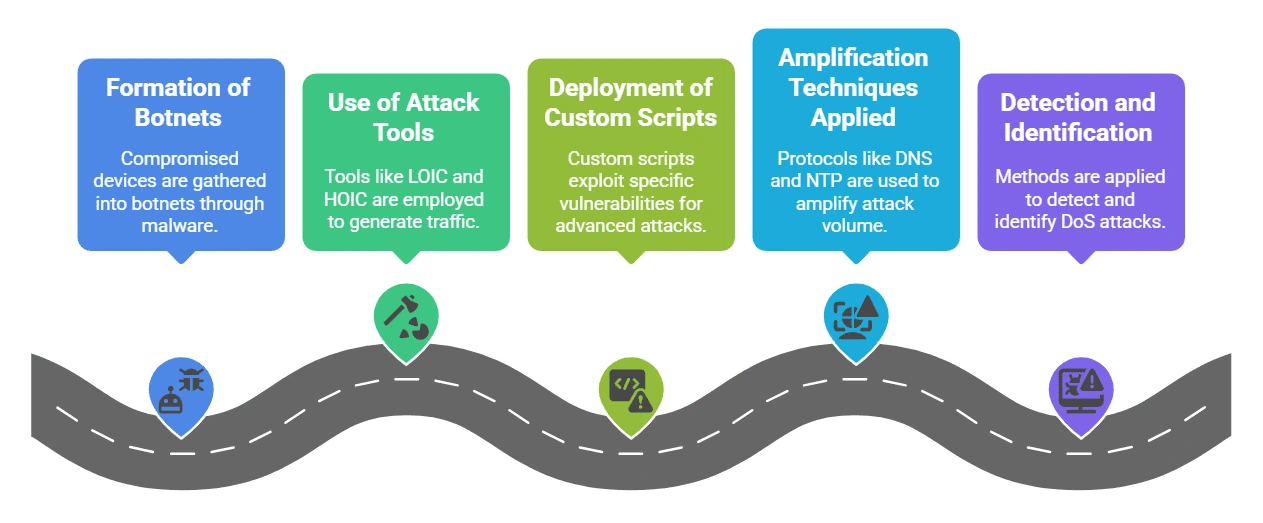 Botnets and Malware
Botnets and MalwareBotnets, formed by compromised devices through malware infections, are frequently used to launch large-scale DDoS attacks. These devices, often unaware of their involvement, collectively flood targets with traffic. The infamous Mirai botnet is a prime example of how IoT devices can be weaponized.
From botnets, we now transition to the specific attack tools and scripts used by adversaries.
Tools such as LOIC (Low Orbit Ion Cannon) and HOIC (High Orbit Ion Cannon) are widely available, allowing even less-skilled attackers to generate significant traffic. In more advanced cases, custom scripts (written in languages like Python or Perl) are deployed to exploit specific vulnerabilities, often integrated with frameworks such as Metasploit.
After reviewing the tools, let’s examine how amplification techniques can further intensify an attack.
Attackers use amplification techniques to magnify their impact. By leveraging protocols like DNS, NTP, or SSDP, a small spoofed request can generate a disproportionately large response, effectively multiplying the attack’s volume. This reflection method makes mitigating the assault significantly more challenging.
With the attack mechanisms clarified, we now move on to how these threats can be detected and identified.
Let’s start by identifying the common indicators that signal a potential DoS attack.
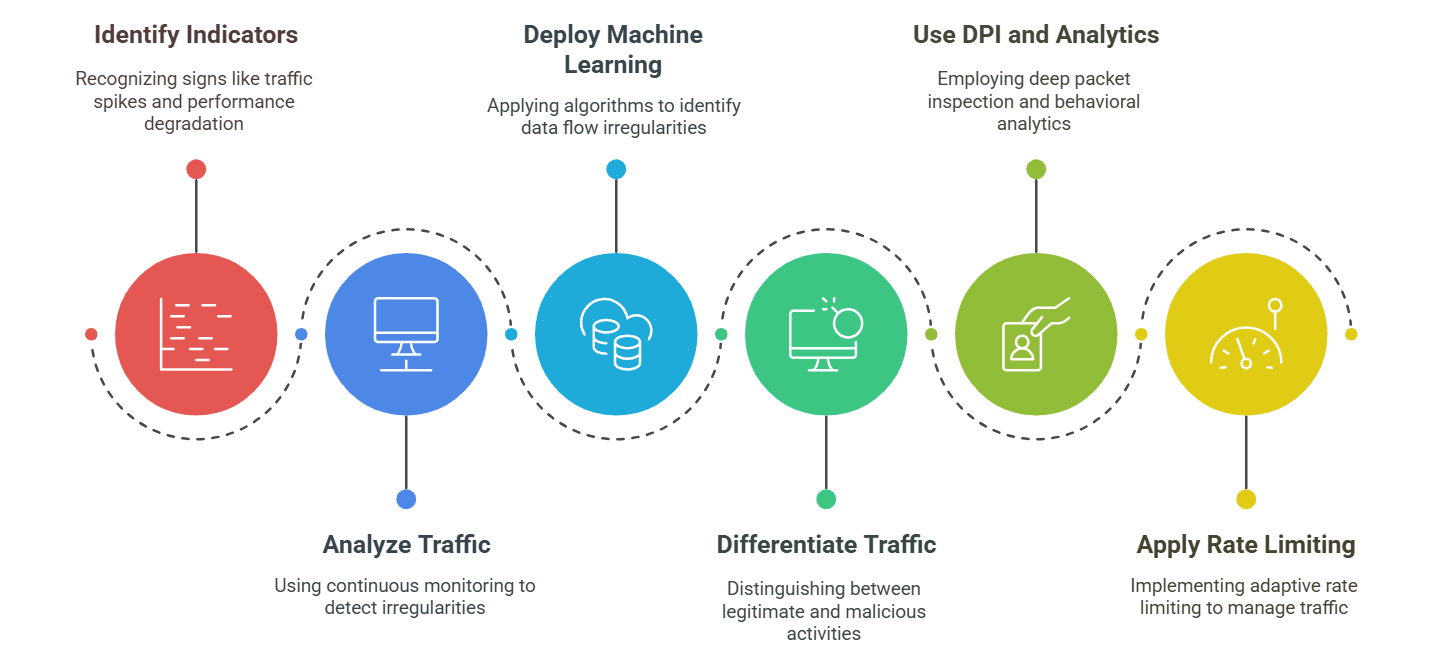
Key signs include sudden traffic spikes, abnormal patterns like repeated requests from a single IP address, and degraded system performance. These indicators signal the need for immediate investigation.
Having pinpointed the indicators, the next step is to look at how traffic analysis and monitoring can confirm an attack.
Continuous, real-time traffic analysis is vital. Advanced systems deploy machine learning algorithms to detect irregularities in data flow and alert administrators to potential threats, enabling rapid response before an attack can fully take hold.
With traffic patterns under scrutiny, it’s essential to differentiate between legitimate users and malicious activity.
Sophisticated systems use deep packet inspection (DPI) and behavioral analytics to distinguish between normal user activity and anomalous behavior. Techniques such as whitelisting and adaptive rate limiting further refine this differentiation, ensuring that legitimate traffic is not inadvertently blocked.
Equipped with detection methods, we can now discuss strategies to prevent and mitigate these attacks.
Let’s begin by exploring how rate limiting and traffic filtering serve as critical defense mechanisms.
 Rate Limiting and Traffic Filtering
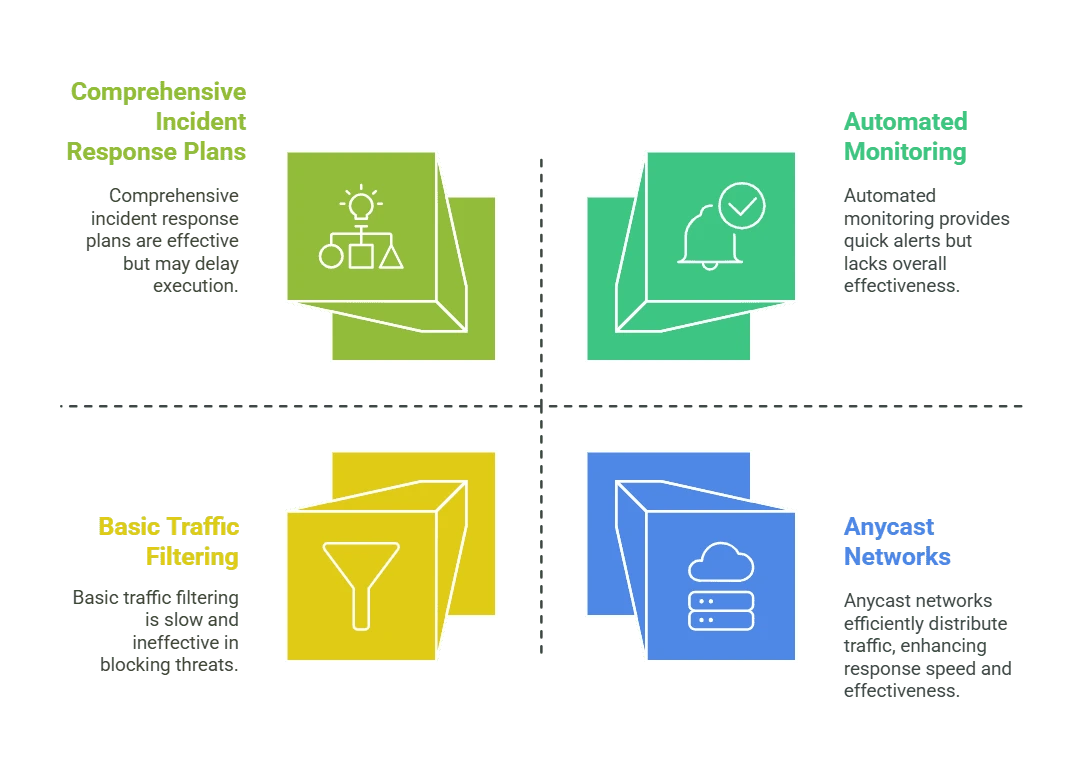
Rate Limiting and Traffic FilteringImplementing rate limits helps control the number of requests a server handles, preventing overload. Traffic filtering, based on IP reputation and request patterns, enables systems to identify and block malicious traffic while ensuring genuine users maintain access.
After discussing rate limiting, we now shift our focus to the advantages of using anycast networks.
Anycast networks distribute incoming traffic across multiple servers, reducing the risk of any single point of failure. This method not only improves load balancing and reduces latency but also provides an effective buffer during large-scale attacks by rerouting traffic to unaffected servers.
With anycast networks in play, let’s consider the importance of having a robust incident response and recovery plan.
A robust incident response plan is essential for minimizing downtime. This plan should include:
Having covered prevention and response, we now answer some frequently asked questions to round out our discussion on DoS attacks.
It stops a network from working normally by using too many resources. The effects could include lost services, money lost from downtime, and damage to the company’s image. In the worst situations, data damage or loss may happen.
Unusual traffic spikes, slow system responses, incomplete connection requests, and general worsening performance are all common signs. These signs need to be looked into right away.
It attacks come in many forms, including buffer overflow, flood, application layer, protocol, burst, and cloud-based attacks. Each one takes advantage of a different weakness in the system.
Rate limiting, traffic filtering, deep packet inspection, anycast networks, and a well-practiced incident reaction plan are some of the ways that organizations can protect themselves from DoS attacks.
ISPs can help stop this attacks by putting in place traffic monitoring at the edge of their networks, providing anti-DDoS services, and working with cybersecurity teams to find and stop malicious traffic as soon as possible.
Some of the most important signs are a quick increase in traffic, a lot of connection requests that aren’t completed, requests from the same IP address over and over, and a clear drop in system performance.
Legitimate surges tend to happen at known times or in response to known events or ads. On the other hand, this attacks often involve unpredictable, long-lasting traffic spikes and strange request behaviors. This can be told apart with the help of advanced tracking and behavioral analytics.
Setting up automated detection and warning systems, making sure response teams know their clear roles and responsibilities, testing the response plan on a regular basis, and making sure there are backups and redundancies in place are all good ideas.
Anti-DDoS services in the cloud can be very useful because they can absorb and spread malicious data across many networks. Because they can grow and change in real time, they are an important part of protecting against large-scale threats.
After an attack, businesses should do full forensic investigations, update their security policies, fix any known vulnerabilities, go over their incident response plans again, and think about taking extra steps like better monitoring and using stronger anti-DDoS services.
To deepen your cybersecurity expertise, consider enrolling in our Cybersecurity Certification Course or the CEH Certification – Certified Ethical Hacking Course.
 Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUPedureka.co