Cyber Security and Ethical Hacking Internship ...
- 15k Enrolled Learners
- Weekend/Weekday
- Live Class
Did you know that 98% of web applications are vulnerable to cyberattacks? As cyberattack practices are becoming more sophisticated with evolving technologies, it is important to run frequent system and server scans to search for potentially vulnerable access points and fix them. This is where vulnerability assessment proves its significance.
Join us on this insightful read, where we delve into analyzing vulnerability in ethical hacking, dissect its importance as a risk management tool and navigate other crucial aspects to demystify vulnerability assessment.

Vulnerability assessment enables ethical hackers to actively identify, assess, and rank weaknesses present in computer systems, applications, and networks. It serves as a fundamental component of ethical hacking, providing us with essential insights to enhance system security and defend against potential threats from malicious entities.

Since vulnerability assessment is a structured analysis of computer systems and networks to find potential system weaknesses, any organisation’s defense strategy heavily relies on vulnerability analysis. It acts as a proactive process that evaluates weak spots before cybercriminals exploit them.
Here’s how vulnerability assessment in cyber security helps:
Organisations can ensure a comprehensive approach to cyber defence by recognising the four main types of vulnerability.
The four main types of vulnerabilities include:
Understanding these vulnerabilities allows ethical hackers to tailor their security strategies accordingly. Thus, they are better equipped for robust protection against potential threats.
Related post Building a simple vulnerability scanner
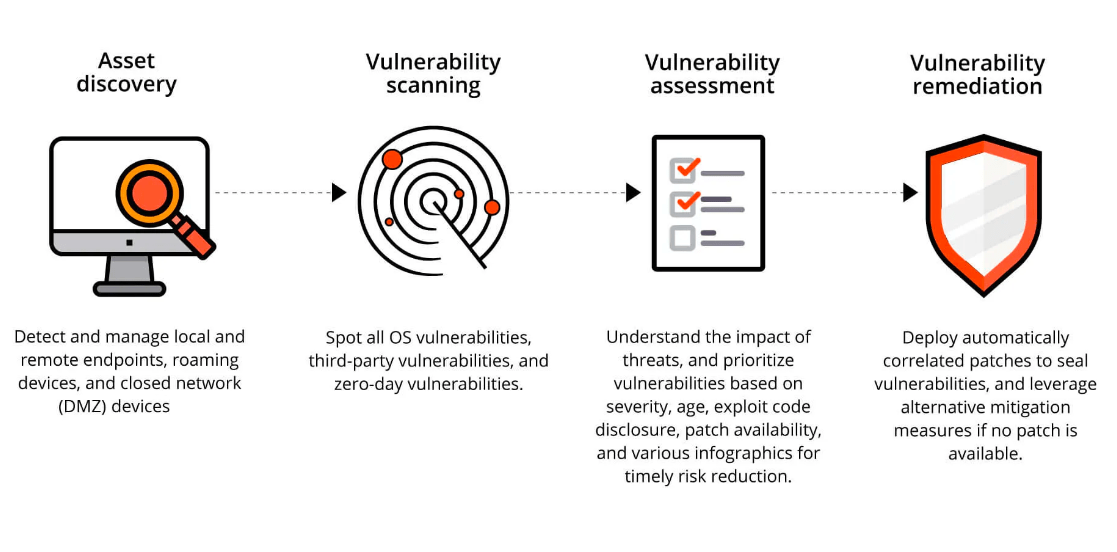
Through a structured approach, vulnerability analysis aims to bolster the IT environment against cyber threats. Here’s a brief step-by-step approach that ethical hackers harness for vulnerability analysis.
Pinpointing vulnerabilities across systems, networks, and applications
Assessing the impact and exploitability of these vulnerabilities
Sorting vulnerabilities by their severity and potential damage
Advising on or implementing fixes to mitigate risk
Maintaining robust cybersecurity defences necessitates this methodical approach. Are you aspiring to delve deeper? Explore a career in ethical hacking: a field that presents the chance, not just an opportunity, but a real chance, to effect significant change by securing digital spaces.
Related Post Creating a custom Metasploit payload to bypass antivirus detection
After exploring inherent vulnerability assessment meaning, knowing its various types can further help you understand how it grants protection against cyberattacks. Let’s explore the various types of vulnerability analysis:
Host-based scans critically secure individual systems by examining specific computers or servers for vulnerabilities in their software, operating systems, and configurations. This process is done by installing individual scanners on the host systems.
Network scan refers to a vulnerability assessment which runs an assessment to identify system or network weaknesses. From routers to firewalls, network scan assesses the network infrastructure for vulnerabilities that might jeopardise the entire organisational network.
This study concentrates on the security of wireless networks. It discerns potential entry points for unauthorised access or data interception by evaluating and classifying records for any detected wireless devices.
The identification of vulnerabilities in database systems, which could potentially result in unauthorised data access or loss, is an essential measure to tackle any possible intrusion. Database scanning, in this case, forms a robust bedrock for safeguarding sensitive information. The process involves running an assessment on databases using proper credentials to retrieve a comprehensive view.
This type of vulnerability assessment actively searches for common attack vectors, such as SQL injection or cross-site scripting in web and software applications, with the help of automated scanning tools (for example: Acunetix, AppScan, and Blacklock). These tools are approved as a Dynamic Application Security Testing (DAST) category tool which adds to their credibility.
Understanding these vulnerability assessment types can help organisations select the appropriate method for their specific needs. However, for those looking to build a career in this field, ethical hacking can be an exceptional choice to acquire a broader perspective. It will give you deeper insights into securing various aspects of IT infrastructure and judging the early signs of malicious intrusion.
The web is fraught with common and uncommon vulnerabilities that could range from simple intrusion to embed bugs to stealing organisational data on a large scale. As of the first week of 2024 itself, global web users discovered around 612 new IT vulnerabilities.
Here are some of the most common vulnerabilities that testers often come across. These include:
Addressing these vulnerabilities is paramount in safeguarding web applications against breaches.
In order to address the listed vulnerabilities, ethical hackers require a diverse catalogue of vulnerability assessment tools. Here are some of the most prominent ones in the industry:
Automate the entire vulnerability assessment process by harnessing leading assessment tools. These tools are essential for efficiently pinpointing vulnerabilities.
Now that we possess a thorough understanding of vulnerability assessment, what exactly makes it different from the role of a penetration tester. Here’s how you can understand the difference between vulnerability assessments and penetration tests:
| Feature | Vulnerability Assessment | Penetration Test |
| Objective | To identify, quantify, and prioritise vulnerabilities in a system or network | To exploit vulnerabilities in a controlled environment to understand the impact of an attack |
| Scope | Broad, aimed at discovering as many vulnerabilities as possible | Narrow, focused on exploiting vulnerabilities to gauge the depth of a potential security breach |
| Approach | Non-intrusive, with the goal of finding potential security weaknesses | Intrusive, with the goal of breaching the system using vulnerabilities |
| Methodology | Automated scanning tools and manual reviews to identify known vulnerabilities | Simulated cyberattacks based on identified vulnerabilities to test the system’s defences |
| Outcome | A list of identified vulnerabilities, their severity, and potential impact | Demonstration of how an attacker could exploit vulnerabilities and the potential consequences |
| Frequency | Regularly scheduled to ensure continuous security posture monitoring | Performed periodically or in response to significant changes in the system or environment |
| Benefit | Provides a comprehensive view of an organisation’s security vulnerabilities | Offers insights into the effectiveness of the existing security measures and potential attack paths |
| Focus | Broad focus on all potential vulnerabilities | Focused on critical vulnerabilities that could be exploited by an attacker |
An irreplaceable aspect of cybersecurity, vulnerability assessment works as a proactive approach to defeating the growing number of cyberattacks. It identifies and mitigates potential threats by understanding and implementing effective strategies in vulnerability analysis. Thus, organisations can make remarkable changes to their security stance.
Are you venturing into the realm of cybersecurity?
Take a transformative step with Edureka’s CEH certification training to kickstart your preparation for CEH or Certified Ethical Hacker qualification. This certification equips one with the knowledge and skills to face vulnerability assessment challenges directly, helping you shape the future of digital security.
Identification, analysis, prioritisation and remediation are the stages that constitute the very core of the existence of the vulnerability assessment process.
Some of the widely implemented methods of vulnerability analysis include:
Nessus, Qualys Guard, and OpenVAS stand as popular vulnerability assessment tools. Each of these presents unique features for conducting thorough vulnerability scanning.
Related post Tools for patching vulnerabilities
 Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUPedureka.co