Full Stack Development Internship Program
- 29k Enrolled Learners
- Weekend/Weekday
- Live Class
Blockchain is the latest buzz words in the market. Bitcoin is great, but the potential of the underlying technology is immense. Something that started as an evolution is soon going to cause a revolution. Investors are cashing in huge amount because they understand the fortune of this ingenious technology is pretty bright. Industry experts and tech enthusiasts are coming up with the blockchain-based products every next day. So wait not, and get industry-ready with these Blockchain Interview Questions.
So, if you are planning to start your Blockchain career, now is the right time to get your Blockchain certification and dive in, when the technology is in its nascent state.
In this Blockchain interview questions blog, I have collected the most frequently asked questions by interviewers. These questions are collected after consulting with top industry experts in the field of Blockchain & related technologies.
For your convenience and better readability, I have divided the interview questions into the following sections:
You may go through this recording of Blockchain Interview Questions and Answers where our instructor has explained the topics in a detailed manner with examples that will help you to understand this concept better.
This Edureka Blockchain Interview Questions and Answers will help you to get succeed in the Blockchain Interviews
The blockchain is a decentralized distributed database of immutable records. The technology was discovered with the invention of Bitcoins(the first cryptocurrency). It’s a trusted approach and there are a lot of companies in the present scenario which are using it. As everything is secure, and because it’s an open-source approach, it can easily be trusted in the long run.
| Topics | Bitcoin | Ethereum |
| Concept | Digital Currency | Smart Contracts |
| Founder | Satoshi Nakamoto | Vitalik Buterin |
| Release Method | Genesis Block Mined | Presale |
| Cryptocurrency Used | Bitcoin(Satoshi) | Ether |
| Algorithm | SHA-256 | Ethash |
| Blocks Time | 10 Minutes | 12-14 Seconds |
| Scalable | Not yet | Yes |
It enables the information to be distributed among the users without being copied.
Blockchains are of three types:
These records are block records and transactional records. Both these records can easily be accessed, and the best thing is, it is possible to integrate them with each other without following the complex algorithms.
| Properties | Blockchain | Traditional Database |
| Operations | Only Insert Operations | Can perform C.R.U.D. operations |
| Replication | Full Replication of block on every peer | Master Slave Multi-Master |
| Consensus | Majority of peers agree on the outcome of transactions | Distributed Transactions (2 phase commit) |
| Invariants | Anybody can validate transactions across the network | Integrity Constraints |
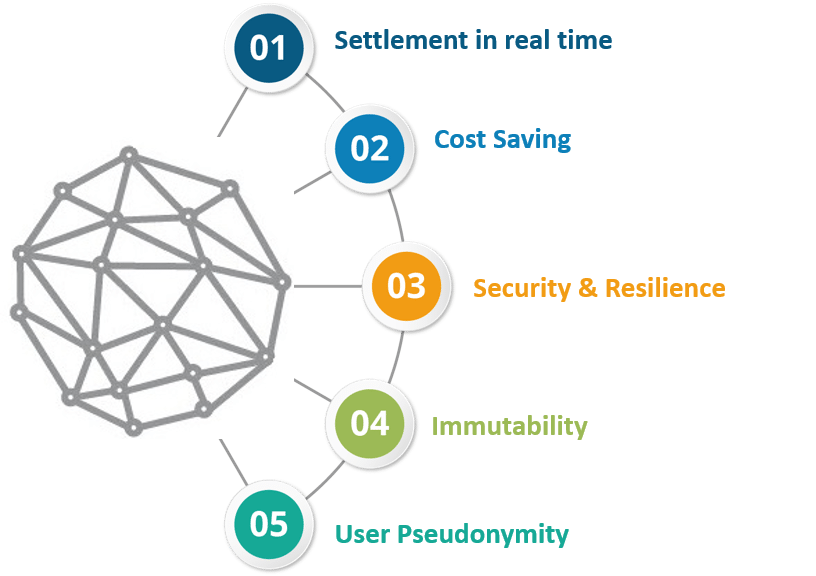
There are four key features of blockchain:
Data security always matters. Encryption is basically an approach that helps organizations to keep their data secure.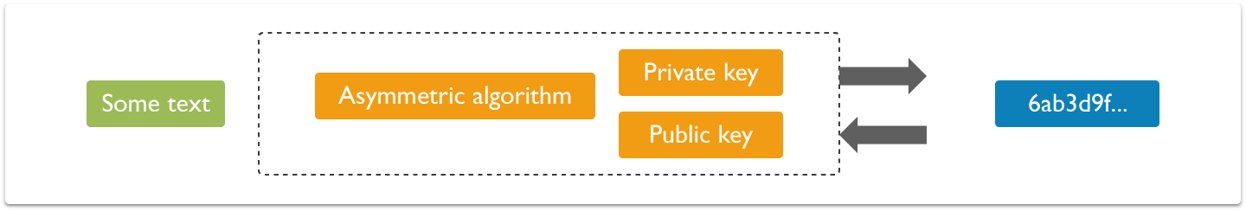 The encrypted data is encoded or changed up to some extent before it is sent out of a network by the sender and only authorized parties can access that information.In Blockchain, this approach is useful because it simply adds more to the overall security and authenticity of blocks and helps to keep them secure.
The encrypted data is encoded or changed up to some extent before it is sent out of a network by the sender and only authorized parties can access that information.In Blockchain, this approach is useful because it simply adds more to the overall security and authenticity of blocks and helps to keep them secure.
Blockchain consists of a list of records. Such records are stored in blocks. These blocks are in turn linked with other blocks and hence constitute a chain called Blockchain.
Every block in this online ledger basically consists of a hash pointer which acts as a link to the block which is prior to it, transaction data and in fact a stamp of time.
No, it’s not possible to do so. In case any modification is required, the organization simply has to erase the information from all other blocks too. It is because of no other reason than this, data must be given the extreme care of while using this approach.
In Blockchain, blocks can be identified by the block header hash and the block height.
Yes, it can be done. There are times when only a specific portion of this online ledger is to be considered. With the help of default options and filters, this can easily be done without making a lot of efforts.
Well, a block or the entire blockchain is protected by a strong cryptographic hash algorithm. Each block has a unique hash pointer. Any modification in the block constituents will result in the change in the hash identifier of the block. Therefore, it offers an excellent level of security. Thus, one needs not to worry about the safety as well as the security of data that is present in a block.
Merkle Tree also known as ‘hash tree’ is a data structure in cryptography in which each leaf node is a hash of a block of data, and each non-leaf node is a hash of its child nodes.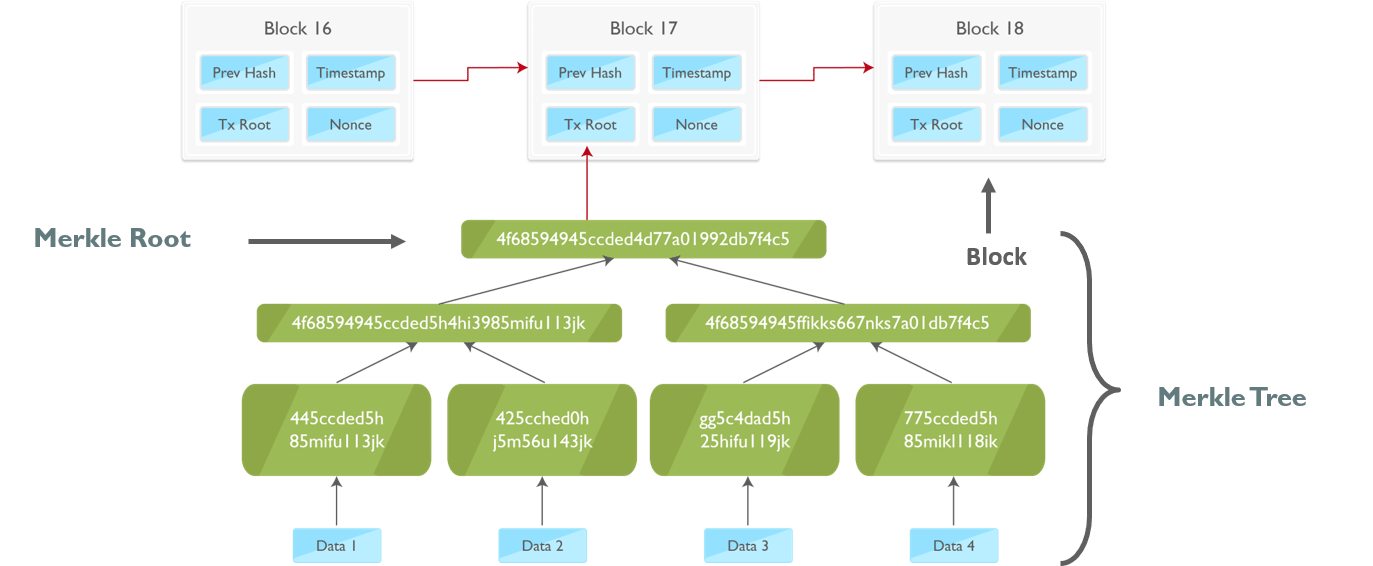
The benefit of using the Merkle Tree in blockchain is that instead of downloading every transaction and every block, a “light client” can only download the chain of block headers.
Also, if someone needs to verify the existence of a specific transaction in a block, then he doesn’t have to download the entire block. Downloading a set of a branch of this tree which contains this transaction is enough. We check the hashes which are just going up the branch (relevant to my transaction). If these hashes check out good, then we know that this particular transaction exist in this block.
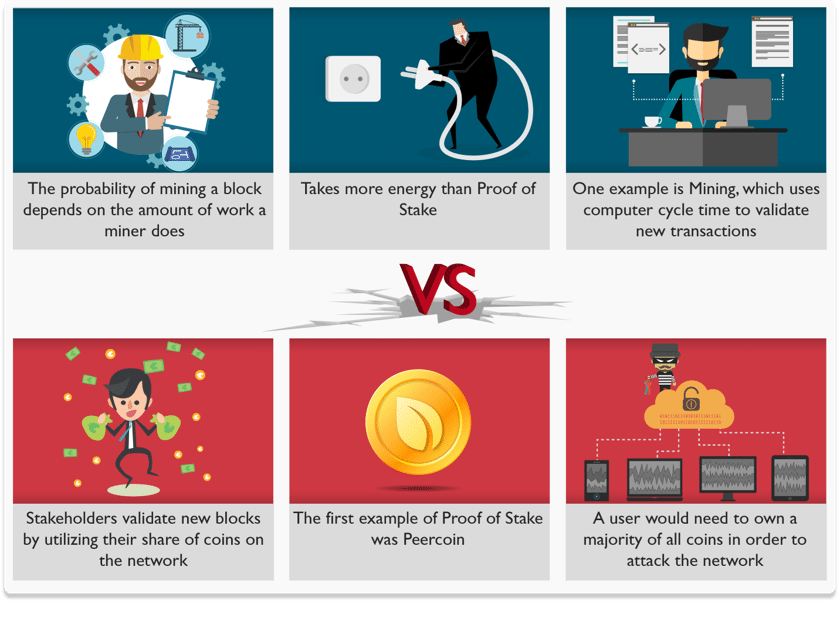
Blockchain is considered incorruptible. Any ill-intentioned individual acting alone is powerless. “To take over the network, an attacker would have to control more than 50 percent of its total computing power,” Augier explains. “We hope that’s a theoretical scenario, but we can’t be sure. Should it happen, the individual would take every precaution to avoid being noticed.” Not to mention the energy required to power the computers needed for the blockchain system to work.
These are:
Q 18. How is a blockchain ledger different from an ordinary one?
The first and in fact the prime difference is Blockchain is a digital ledger that can be decentralized very easily. The chances of error in this approach are far less than that in an ordinary ledger. An ordinary ledger is what that is prepared by hands or by human efforts while the Blockchain performs all its tasks automatically. You just need to configure it in a proper manner and by following all the guidelines.
There is no restriction on keeping records of any type in the Blockchain approach. Industries are using Blockchain for securing all types of records.
The common types of records (to name a few) that can be kept on the Blockchains are:
The system relies on the network servicing protocol and the nodes of the network.
Ready to discover the Top 10 Highest Paying Jobs for 2025? In this video, we’re uncovering the most lucrative and in-demand careers like AI & ML Engineers , Cybersecurity Engineers , Data Scientists , Cloud Architects , and Blockchain Developers! Not only will you learn about the skills you need to land these roles, but we’ll also reveal the salary potential for each job. Whether you’re looking to switch careers or climb the job ladder, this video will show you the path to a high-paying, future-proof career! Don’t miss out—watch now!
Following are the components of blockchain Ecosystem:
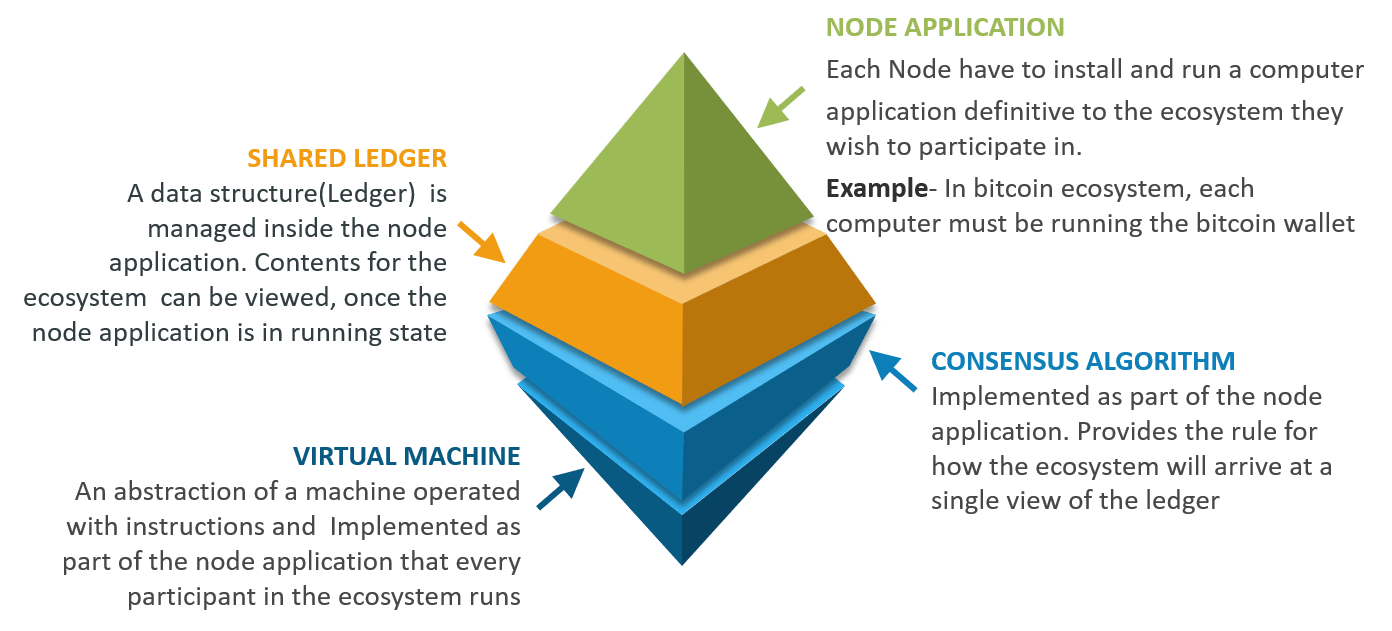
After the development of bitcoin, various blockchain platforms started coming up. Ethereum came right after the evolution of Bitcoins, and is one of the popular public platforms for building Blockchain based applications.
Then there is a Hyperledger community for building enterprise-based solutions. Also, Qtum, IOTA, EOS are some of the widely used platforms for building Blockchain.
It’s a condition when one digital token is spent multiple times because the token generally consists of a digital file that can easily be cloned. It simply leads to inflation and organizations must bear a huge loss. One of the primary aims of Blockchain technology is to eliminate this approach up to the possible extent.
Blockchain prevents double spending by confirming a transaction by multiple parties before the actual transaction is written to the ledger. It’s no exaggeration to say that the entirety of bitcoin’s system of Blockchain, mining, proof of work, difficulty etc, exist to produce this history of transactions that is computationally impractical to modify.
A hash pointer to the previous block
Timestamp
List of transactions
All of the above [Ans]
A flat file
A Database
Both of the above [Ans]
None of the above
Backward to the previous block [Ans]
Forward to next block
Not linked with each other
SHA128
SHA256 [Ans]
Multiple parent blocks
Multiple children blocks [Ans]
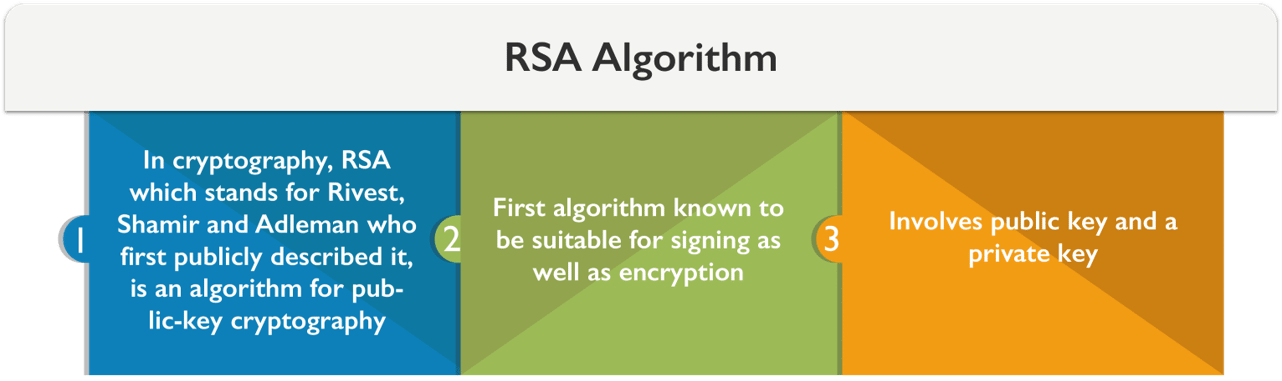
Security of R.S.A.
There are different approaches used in attacking the RSA algorithm:
It is a form of digital signature in which the content of a message is disguised (blinded) before it is signed. The resulting blind signature can be publicly verified against the original, unblinded message in the manner of a regular digital signature.
Blind signatures are typically employed in privacy-related protocols where the signer and message author are different parties. Examples include cryptographic election systems and digital cash schemes.
It is a well-known fact that security matters a lot in digital transactions. Secret sharing is an approach meant for same. In Blockchain technology it is an approach that divides secret or personal information into different units and sent them to the users on the network.
The original information can only be combined when a participant to whom a share of the secret is allocated agree to combine them together with others. There are several security-related benefits it can offer in Blockchain technology.
An off-chain transaction is the movement of value outside of the blockchain. While an on-chain transaction – usually referred to as simply ‘a transaction’ – modifies the blockchain and depends on the blockchain to determine its validity an off-chain transaction relies on other methods to record and validate the transaction.
Executive accounting is nothing but a special type of accounting which is designed exclusively for a business that offers services to the people. There is no strict upper limit on services and a business can manage any through the executive accounting. Blockchain has algorithms that are specially meant to handle executive accounting. In fact, it cut down many problems that are associated with the same.
There are lots of threats to information in the present scenario. Due to increase in online transactions over the internet, many hackers have become active and are adopting new approaches to hack information and servers that contain financial information.
The major threat is software attack, identity theft, information extortion, as well as sabotage. In addition to this, Trojan horses, worms, and viruses are other trouble creators.
It is basically a process of finding the threats and all the vulnerabilities to the financial records of an organization. The best thing that can be done with this approach is to take the right countermeasures against them immediately.
Another approach is to pay attention to a backup plan. Based on the value of information, more approaches such as buying new risk management software can simply be considered. The prime risk to information is from black-hat hackers.
51% Attack refers to a situation where a group of miners who hold more than 50% of the Network Hash Rate could manipulate with the New transactions (Stopping the transactions to proceed or gaining conformations) or able to reverse the transactions that were recently confirmed and kind of doing Double spend. It is Highly unlikely to be able to do that today but it is possible.
An information leak can cut down the reputation of an organization up to an excellent extent. In addition to this, it can be the reason for organization bearing huge losses. Many organizations who fail to implement security protocols to keep their data secure have already lost the trust of their customers and are struggling very hard to get the same reputation again. The overall profits of any organization can reduce up to 80% if no attention is paid to the online transaction security.
The information is often shared on a network. Before actually transmitting it over a network, it needs to be changed into formats that can fit the standards of the channels (the channel is a link between the sender and a receiver).
The work done to convert the information at both sender and receiver end is generally regarded as information processing. The biggest challenge to information processing is securing it during that time. Another challenge is processing bulk information can impose a limit on performance.
There is no strict upper limit on the category of business who can consider this approach. The fact is almost all the businesses are engaged in online or financial transactions that they need to make to run the processes smoothly. Large-scale corporations, financial institutions, private businesses, government departments and even defense organizations can trust this technology very easily.
A business blockchain requires a shared ledger, smart contract functionality, privacy and trust.
Q 14. What are the key principles in Blockchain that are helpful in eliminating the security threats that needs to be followed?
Yes, there are a few principles that need to be followed with respect to time. They are:
1.Auditing
2.Securing applications
3. Securing testing and similar approaches
4. Database security
5. Continuity planning
6. Digital workforce training
All these principles are basic and are easy to implement. They are helpful in making the transactions records useful.
A security policy defines what exactly needs to be secured on a system. It bounds a network user under some core protocols that they all must agree and follow to enhance the overall security. When it comes to information or financial records of an organization, multiple security policies are implemented than just one.
Banks and accounting systems use ledgers to track and timestamp transactions. The difference is that the blockchain is completely decentralized and an open source. This means that people do not have to rely on or trust the central bank to keep track of the transactions. The peer-to-peer blockchain technology can keep track of all the transactions without the fear of having them erased or lost.
Furthermore, the blockchain, because of its open-source nature, is more versatile and programmable than central banking ledgers. If programmers need new functionality on the blockchain, they can simply innovate on top of already existing software through consensus. This is difficult for central banks because of all of their regulations and central points of failure.
Now, the possible reasons why we need consensus mechanism more than “proof-of-work” are”
There is no specific condition of using it. However, the network must be a peer-to-peer network under the concerned protocols. It validates the new block simply and helps organizations to keep up the pace in this matter without investing in third-party applications.
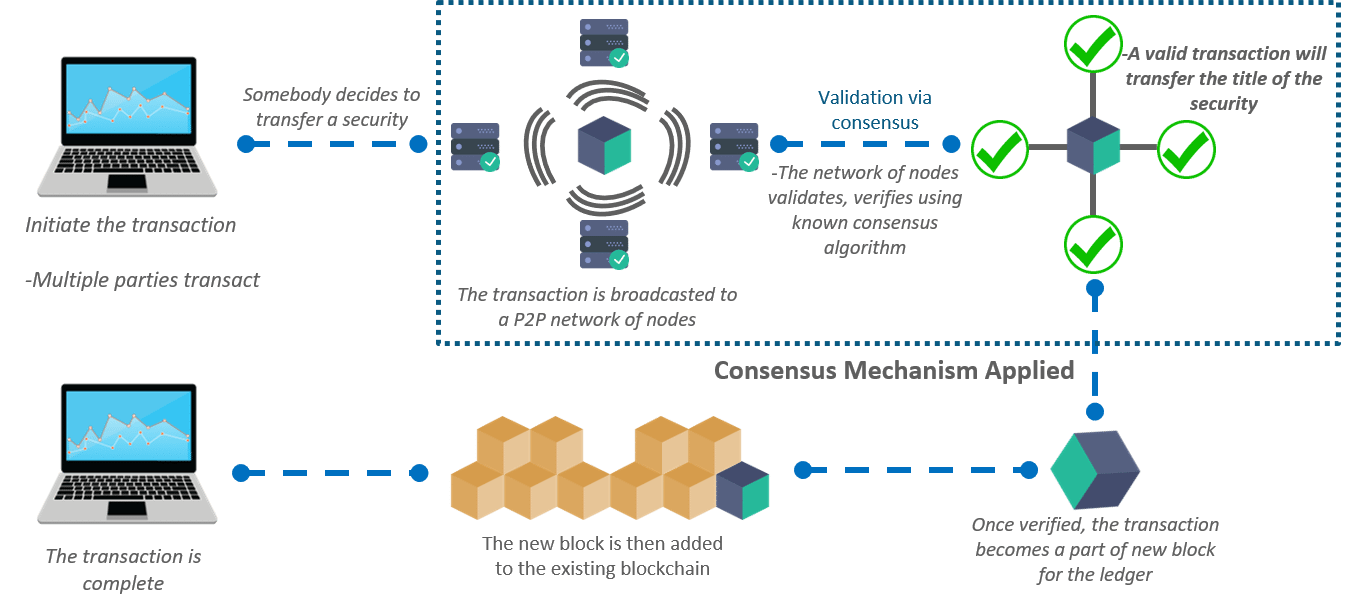
Well, there are total six steps involved in this process and they are:
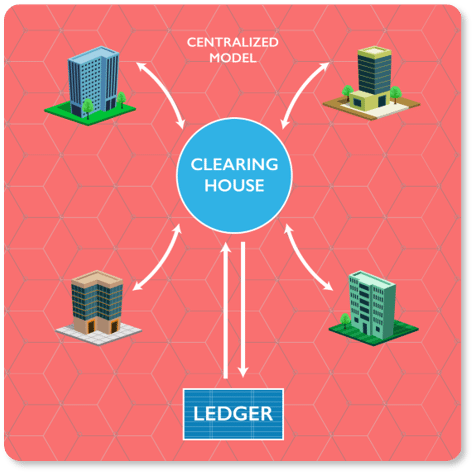
Blockchain in Stock Market
Problems in Present Stock Market:
Centralized and expensive
Limited Transparency
How Blockchain solves the problem
The centralized hub can be removed and the blockchain can be used to directly transfer share ownership between investors.
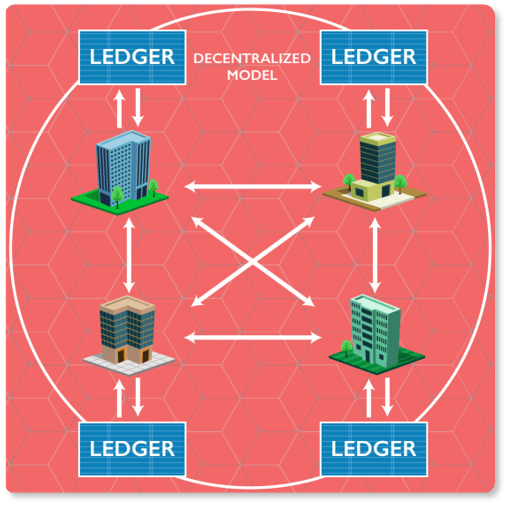
A ledger updated in minutes could save millions in collateral and settlement costs, while also automating banks’ creaky and expensive back office systems.
Good work! You have a solid understanding of this important emerging technology!!

Got a question for us? Please mention it in the comments section and we will get back to you at the earliest.
If you wish to build a career in the domain of Blockchain and gain expertise in Blockchain technology, get enrolled in live-online Blockchain Training in Bangalore here, that comes with 24*7 support to guide you throughout your learning period.
 Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUPedureka.co



I have one question, in blockchain to have a transaction it is to be verified through consensus then only it can be added, now suppose I want to send money to my friend but nobody is mining the block or suppose nobody is responding so I will not be able to transfer the money.
Is this not a problem ??
Thanks for sharing a very useful interview questions to me and your all readers. Sure i can say very great analyses and collected top best questions.Are you looking the expert blockchain development companies, here you can find the best team who is supportive for all. This provides good impact and thus it shows right solution to overcome the financial tasks smoothly.
One question I have is this: In what form does value gets transferred in blockchain in exchange for good or services, between participants on the network? If money needs to be transferred, would bank accounts have to be linked to the network or must a unique non-monetary platform such as Bitcoin needs to be defined for each blockchain network for transactions?
A blockchain (database) only contains a record of all changes that were ever made to it. Value is ascribed to the fact of actually being able to make such changes. Value in Bitcoin is being transferred just because your business partner would accept and value bitcoins or rather the ability to make more changes to the record. If you need to transfer Dollars, an intermediary is necessary who exchanges bitcoins for Dollars and the other way around, thus taking one or both sides in the value-acceptance-scheme (sender and receiver).
Generally speaking, banks could integrate the Bitcoin blockchain and “link accounts” to it. But a bank would then always be the intermediary. This intermediary is actually made obsolete by the Bitcoin system if a partner accepts bitcoins directly. I suppose you are talking about the gateways from fiat money to bitcoins vice versa (entrance and exit). But I’m not sure to understand the last part of your question, if you might clarify?
Hey Harsha,
In blockchains, values or assets get’s transferred on the basis of set conditions(if you have written a smart code functionality). You cannot link bank account to blockchains, it only works on non- monetary units (or cryptocurrency)
Hope this helps :)
Hey Harsha, When you are creating Blockchains, you create them for a specific coin. If you are creating a new blockchain, you are creating it for a new coin. The blockchain would record transactions for that coin. The monetary value of the coin is either defined by the company/owner creating the blockchain, or like other coins by the supply and demand.
Common practice is to register a new coin in some Crypto wallet, and the wallet software provides the interface with the banks to buy the coins in exchange of fiat currency. You can create a wallet of your own to enable that interface.