Cyber Security and Ethical Hacking Internship ...
- 15k Enrolled Learners
- Weekend/Weekday
- Live Class
If you are a person who is pursuing a career in Information Security, one of the most important things is to have a security-focused operating system. A suitable OS helps you in performing time-consuming and tedious tasks efficiently. Currently, there are countless Linux based OS but Kali Linux is arguably one of the best choices. It is used by cybersecurity experts for penetration testing, ethical hacking, and network security assessments. In this article, we will take a look at how to install Kali Linux.
Let’s take a look at topics covered in this article:
Kali Linux is the industry’s leading Linux distribution in penetration testing, ethical hacking, and security auditing.
When it comes to penetration testing, hacking and offensive Linux distributions, one of the first thing to be mentioned is Kali Linux. The software comes pre-packaged with a variety of different command line hacking tools geared towards various information security tasks. Such as Penetration Testing, Network Security, Computer Forensics, and Application Security. Basically, Kali Linux is the ultimate OS for ethical hackers and is widely recognized in all parts of the world, even among Windows users who may not even know what Linux is.
So, what makes Kali Linux a preferable choice when compared to other Linux distributions like Parrot Security, Backbox, Blackarch, and many others?
How to install Kali Linux?
This Edureka video on “How to install Kali Linux?” will help you understand how to install Kali Linux on different platforms like windows, mac and Linux distributions.
Kali Linux is the most preferred operating system to perform various information security tasks due to the following reasons:
So, because of the above reasons, Kali Linux is the most popular OS used by Cyber Security experts all over the world. If you want to get into the world of Cyber Security and Ethical Hacking, learning how to install and use Kali Linux for ethical hacking is the first step. You can go through this Cybersecurity video lecture where you can find our Training expert is discussing each & every nitty-gritty of the technology. Go through our new CEH Certification Training to explore more about ethical hacking. This training will teach you the most current hacking techniques, tools and methods that hackers use.
What is Cyber Security?
This Edureka video on “What is Cyber Security” gives an introduction to the Cyber Security world and talks about its basic concepts.
This Edureka video on “What is Cyber Security” gives an introduction to the Cyber Security world and talks about its basic concepts. You get to know different kinds of attack in today’s IT world and how cybersecurity is the solution to these attacks.
Let’s start with our Kali Linux Installation!
Kali Linux installation is a fairly simple process and you have multiple installation options. Most preferred ones include:
While you have multiple options to choose from, in this article, we will learn how to install Kali Linux using virtualization software. Following are the below-stated steps, you can set up your machine with all the tools you need to perform a comprehensive penetration test.
Getting Started with Installation
Step 1: Install VMware
In order to run Kali Linux, we will need some sort of virtualization software first. While there are many options to choose from, such as Oracle’s VirtualBox, I prefer using VMware. Once the installation is done, launch VMware from your applications folder.
Step 2: Download Kali Linux and check image integrity
To download Kali Linux you can go to the official download page and select the one that best suits your needs from there. In addition, on the download page, you will find a bunch of hexadecimal numbers. And those are not there for fun. Kali Linux is intended to be used for security-related tasks. So, you need to check the integrity of the image you download.
You should check the SHA-256 fingerprint of the file and compare it with the one provided on the download site.
Step 3: Launch a new virtual machine
On VMware Workstation Pro homepage, click on create a new virtual machine, choose the Kali Linux iso file, select the guest operating system and configure virtual machine details (here, Kali Linux). Start the virtual machine by selecting the Kali Linux VM, and then clicking on the green “Power On” button.
The machine will start up!
To become a trusted cybersecurity professional enroll now in the CISSP Certification Course and get certified.
Step 1: Once the machine is powered up, you will be prompted to select your preferred installation mode in the GRUB menu. Select graphical install and continue.

Step 3: Once through the local information, the loader will automatically install some additional components and configure your network related settings. Then the installer will prompt for a hostname and domain for this installation. Provide appropriate information for the environment and continue installing.
Step 4: Set a password for your Kali Linux machine and hit continue. DO NOT FORGET THIS PASSWORD.
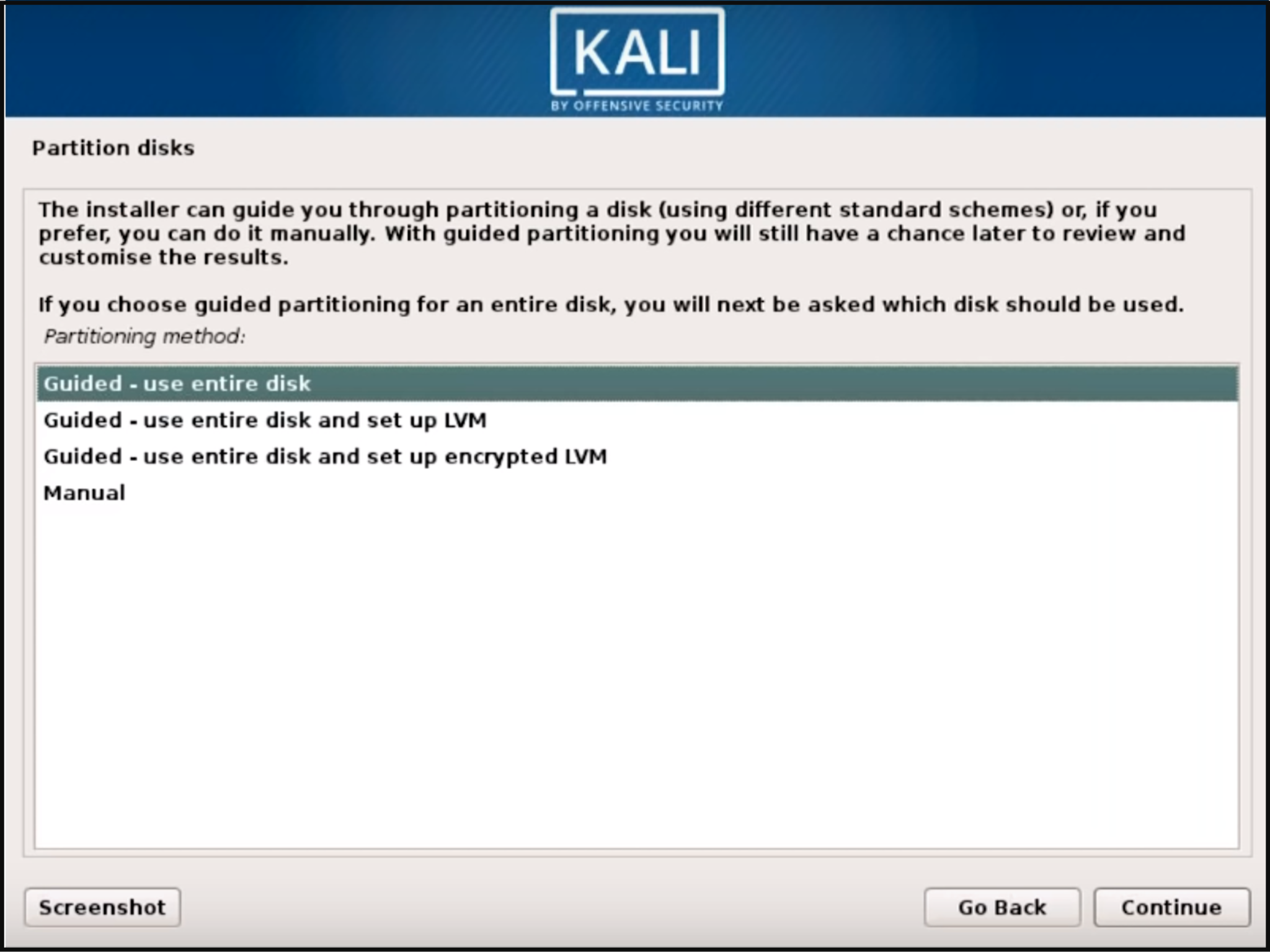
Step 5: After the password is set, the installer will prompt you to set the time zone and then pauses at the disk partitioning. The installer will now provide you four choices about the partitions of the disk. The easiest option for you is to use ‘Guided – Use Entire Disk’. Experienced users can use the “Manual” partitioning method for more granular configuration options.
Step 6: Select the partitioning disk (the recommended option is all files in one partition for new users) & then hit on continue.
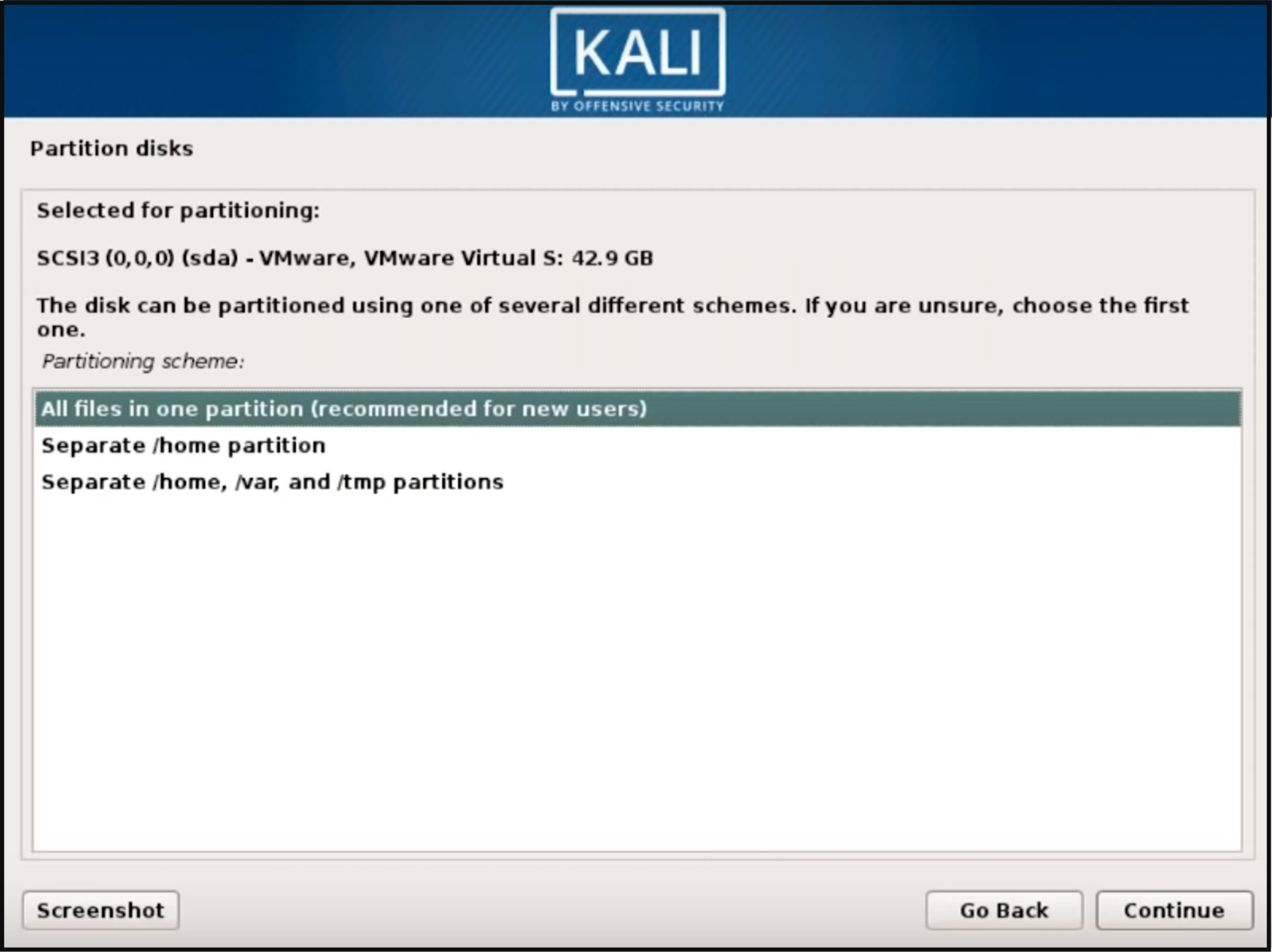
Step 7: Confirm all changes to be made to the disk on the host machine. Be aware that if you continue it will ERASE DATA ON THE DISK.
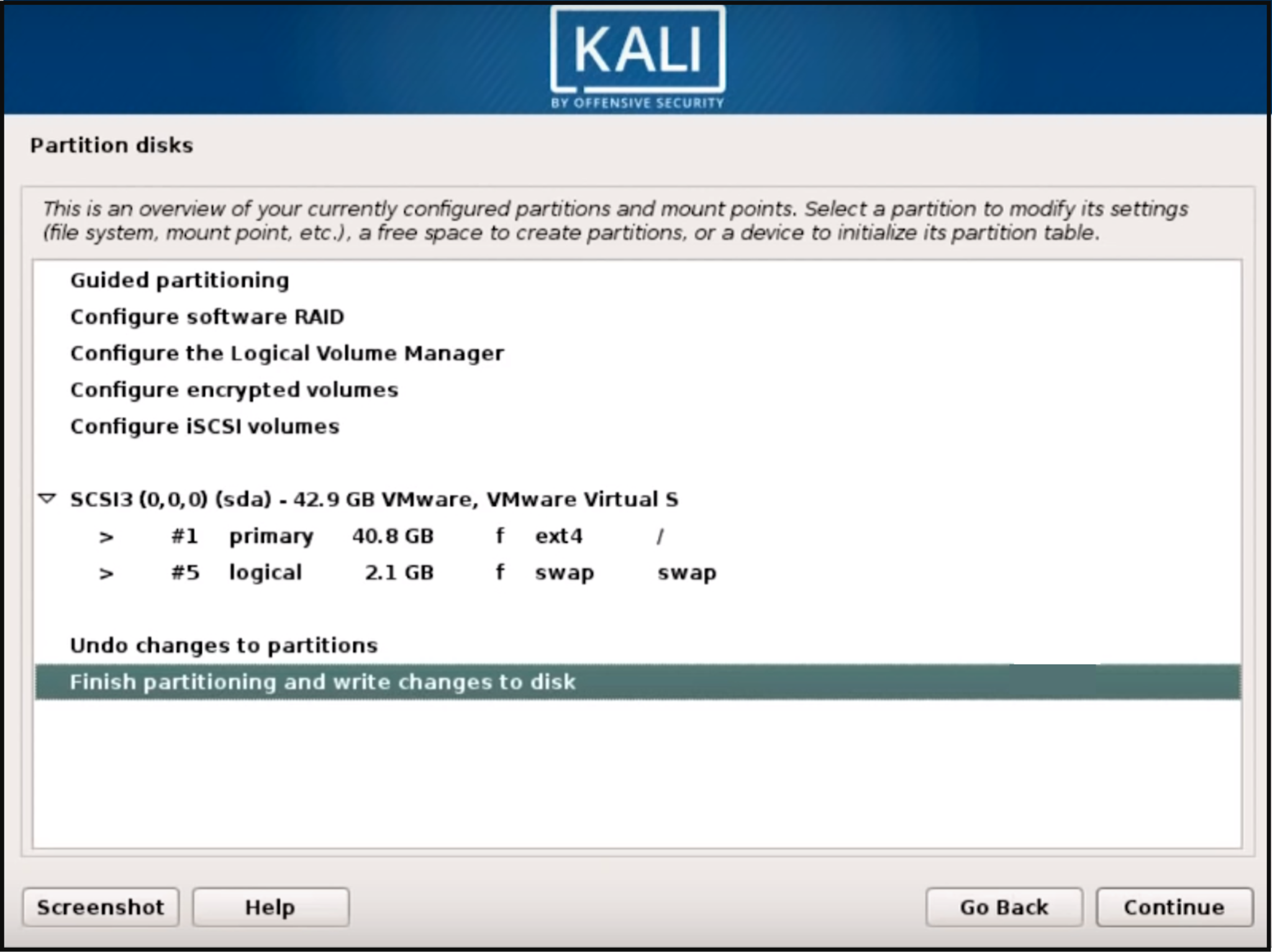
On you confirm the partition changes, the installer will run through the process of installing the files. Let it install the system automatically, this may take a while…
Step 8: Once the necessary files are installed, system will ask you if you want to set up a network mirror to obtain future pieces of software and updates. Be sure to enable this functionality if you wish to use the Kali repositories.
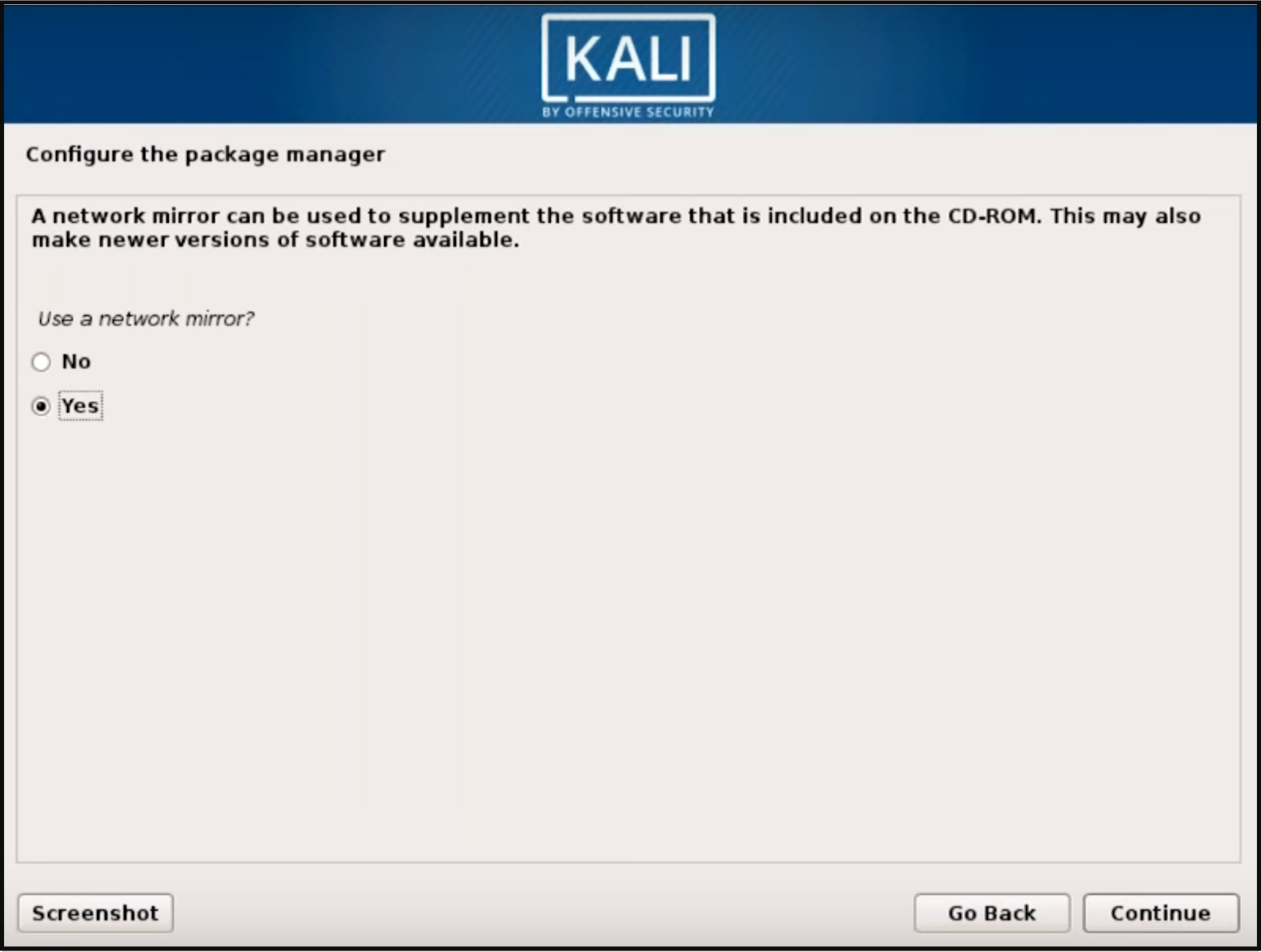
Let it configure the package manager related files then…
Step 9: Next you will be asked to install the GRUB boot loader. Select ‘Yes’ and pick the device to write the necessary boot loader information to the hard drive which is required to boot Kali.
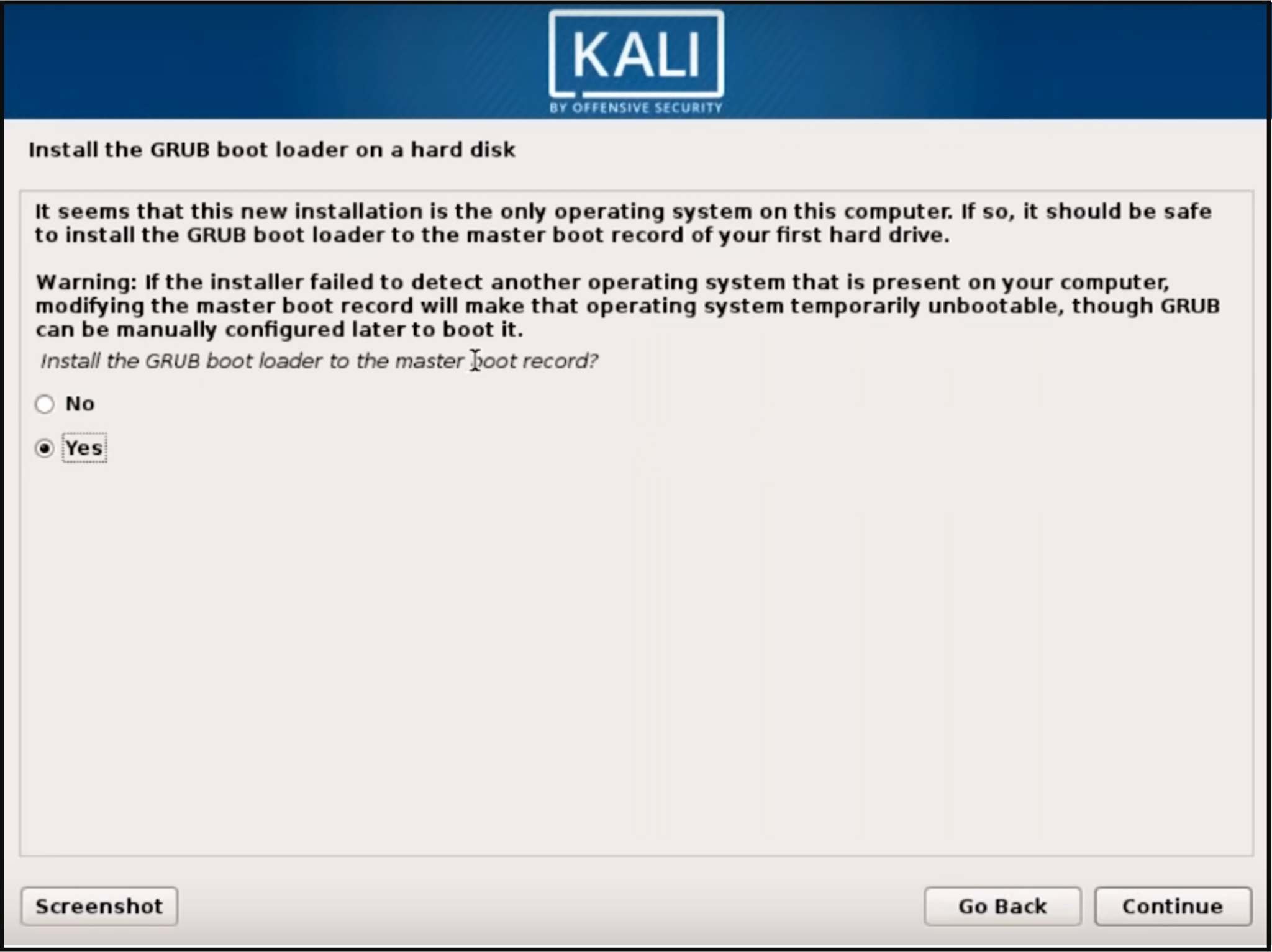
Step 10: Once the installer finishes installing GRUB to the disk, click on continue to finish the installation, it will install some final stage files.
By this point, Kali would be successfully installed and you would be ready to begin your journey exploring Kali Linux!
We have reached the end of “How to install Kali Linux” article. If this has spiked your interest and you want to know more about cybersecurity and ethical hacking, then check out our Cyber Security Certification Training which comes with instructor-led live training and real-life project experience. This training will help you understand cybersecurity in depth and help you achieve mastery over the subject.
You can also take a look at our newly launched CompTIA Security+ Certification Course, which is a first-of-a-kind official partnership between Edureka & CompTIA Security+. It offers you a chance to earn a global certification that focuses on core cybersecurity skills which are indispensable for security and network administrators.
Explore various domains of Cybersecurity through this Cyber Security Internship, including Network Security, Cryptography and Web Application Hacking.
Learn Cybersecurity the right way with Edureka’s Master’s in Cybersecurity program and defend the world’s biggest companies from phishers, hackers and cyber attacks.
 Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUPedureka.co