The dig command is a powerful tool to query DNS servers for information like A, MX, CNAME records, etc.
You can run dig directly from Python using the subprocess module:
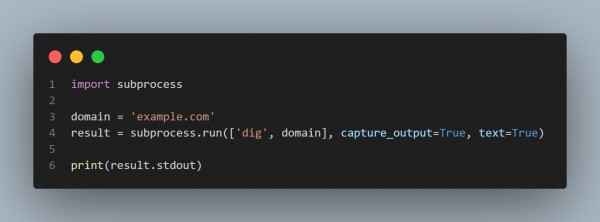
- subprocess.run(['dig', domain]) executes the dig command in the terminal.
- capture_output=True captures the output of the command.
- text=True ensures the output is in string format (not bytes).
This allows you to automate DNS queries from within your Python scripts, useful for DNS footprinting.
 REGISTER FOR FREE WEBINAR
X
REGISTER FOR FREE WEBINAR
X
 Thank you for registering
Join Edureka Meetup community for 100+ Free Webinars each month
JOIN MEETUP GROUP
Thank you for registering
Join Edureka Meetup community for 100+ Free Webinars each month
JOIN MEETUP GROUP