
Ethical Hacking Course in Mumbai






Instructor-led Ethical Hacking Course live online Training Schedule
Flexible batches for you
Why enroll for Ethical Hacking Course in Mumbai?



Certified Ethical Hacker Training Benefits in Mumbai



Why Ethical Hacking Course from edureka in Mumbai
Live Interactive Learning
- 40 Hrs Instructor-Led Training
- World-Class Instructors
- Instant doubt clearing
Course Contents by EC-Council
- Includes CEH v13 Exam Voucher
- 6 months free access to Hands-On Labs
- Course kit includes eCourseware
24x7 Support
- One-On-One Learning Assistance
- Help Desk Support
- Resolve Doubts in Real-time
Hands-On Project Based Learning
- Industry relevant Hands-On Labs
- Modern Case Studies
- Mock Questions
Industry Recognised Certification
- Accredited training partner of EC-Council
- Edureka Training Certificate
- Certificate of Completion
Like what you hear from our learners?
Take the first step!
About your Ethical Hacking Course
Ethical Hacking Skills Covered
Ethical Hacking Tools Covered
CEH Certification Course Curriculum in Mumbai
Curriculum Designed by Experts
Introduction to Ethical Hacking
Topics
- Elements of Information Security
- Classification of Attacks
- Hacker Classes
- Ethical Hacking
- Al-Driven Ethical Hacking
- ChatGPT-Powered Al Tools for Ethical Hackers
- CEH Ethical Hacking Framework
- Cyber Kill Chain Methodology
- MITRE ATT&CK Framework
- Information Assurance (IA)
- Risk Management
- Threat Intelligence Lifecycle
- Incident Management
- PCI DSS
- HIPPA
- SOX
- GDPR
- DPA
![skill you will learn skill]()
- Basics of Ethical Hacking
- Laws and Compliance of Cyber Security
- Information Security Controls
Footprinting and Reconnaissance
Topics
- Reconnaissance
- Footprinting Using Advanced Google Hacking Techniques
- Footprinting through People Search Services
- Dark Web Footprinting
- Competitive Intelligence Gathering
- Footprinting through Social Networking Sites
- Whois Footprinting
- DNS Footprinting
- Traceroute Analysis
- Email Footprinting
- Footprinting through Social Engineering
- Al-Powered OSINT Tools
![Hands On Experience skill]()
- Perform footprinting on the target network using search engines, internet research services, and social networking sites
- Perform whois, DNS, network, and email footprinting on the target network
- Perform Footprinting using Al
![skill you will learn skill]()
- Footprinting techniques
- Reconnaissance methods
- Pre-attack strategies
- Ethical hacking tools
Scanning Networks
Topics
- Network Scanning
- Scanning Tools
- Host Discovery Techniques
- Port Scanning Techniques
- Host Discovery and Port Scanning with Al
- Service Version Discovery, OS
- Discovery/Banner Grabbing
- Scanning Beyond IDS and Firewall
- Scanning Detection and Prevention
![Hands On Experience skill]()
- Perform host, port, service, and OS discovery on the target network
- Perform scanning on the target network beyond IDS and Firewall
- Perform scanning using Al
![skill you will learn skill]()
- Network Scanning Techniques
- Host and Port Discovery
- AI-Powered Scanning
Enumeration
Topics
- Enumeration
- NetBIOS Enumeration
- SNMP Enumeration
- LDAP Enumeration
- NTP Enumeration
- NFS Enumeration
- SMTP Enumeration
- DNS Cache Snooping
- DNSSEC Zone Walking
- IPsec Enumeration
- VoIP Enumeration
- RPC Enumeration
- Unix/Linux User Enumeration
- SMB Enumeration
- Enumeration using Al
- Enumeration Countermeasures
![Hands On Experience skill]()
- Perform NetBIOS, SNMP, LDAP, NFS, DNS, SMTP, RPC, SMB, and FTP Enumeration
- Perform Enumeration using Al
![skill you will learn skill]()
- Enumeration Techniques
- Enumeration using Al
- Enumeration Countermeasures
Vulnerability Analysis
Topics
- Vulnerability Classification
- Vulnerability Scoring Systems and Databases
- Vulnerability-Management Life Cycle
- Vulnerability Research, Vulnerability Scanning and Analysis
- Vulnerability Assessment Tools
- Vulnerability Assessment Reports
- Al-Powered Vulnerability Assessment Tools
![Hands On Experience skill]()
- Perform Vulnerability Research using Vulnerability Scoring Systems and Databases
- Perform Vulnerability Assessment using Various Vulnerability Assessment Tools
- Perform Vulnerability Analysis using Al
![skill you will learn skill]()
- Identify Security Loopholes
- Vulnerability Assessment Tools
- Al-Powered Vulnerability Assessment
System Hacking
Topics
- Password Cracking
- Password Attacks
- Password-Cracking Tools
- Vulnerability Exploitation
- Metasploit Framework
- Al-Powered Vulnerability Exploitation Tools
- Buffer Overflow
- Buffer Overflow Detection Tools
- Active Directory (AD) enumeration
- Privilege Escalation
- Privilege Escalation Tools
- Executing Applications
- Keylogger
- Spyware
- Rootkits
- Steganography
- Steganalysis
- Steganography Detection Tools
- Maintaining Persistence
- Linux and Windows Post Exploitation
- Covering Tracks
- Clearing Logs
- Track-Covering Tools
![Hands On Experience skill]()
- Perform an Active Online Attack to Crack the System's Password
- Perform Buffer Overflow Attack to Gain Access to a Remote System
- Escalate Privileges using Privilege Escalation Tools
- Escalate Privileges in Linux Machine
- Hide Data using Steganography
- Clear Windows and Linux Machine Logs using Various Utilities
- Hiding Artifacts in Windows and Linux Machines
- Perform System Hacking using Al
![skill you will learn skill]()
- System Hacking Methods
- Discover Network Vulnerabilities
- Steganography Techniques
- Steganalysis Attacks
- Covering Tracks Strategies
Malware Threats
Topics
- Malware
- Advanced Persistent Threat Lifecycle
- Trojan
- Virus
- Ransomware
- Computer Worms
- Fileless Malware
- Al-based Malware
- Malware Analysis
- Static Malware Analysis
- Dynamic Malware Analysis
- Virus Detection Methods
- Malware Countermeasures
- Anti-Trojan Software
- Al-Powered Malware Detection and Analysis Tools
![Hands On Experience skill]()
- Gain Control over a Victim Machine using Trojan
- Infect the Target System using a Virus
- Perform Static and Dynamic Malware Analysis
![skill you will learn skill]()
- Advanced Persistent Threats (APT)
- Fileless Malware Techniques
- Malware Analysis Procedures
- Malware Countermeasures
Sniffing
Topics
- Network Sniffing
- MAC Flooding
- DHCP Starvation Attack
- ARP Spoofing
- ARP Spoofing/Poisoning Tools
- MAC Spoofing
- VLAN Hopping
- STP Attack
- DNS Poisoning Techniques
- DNS Poisoning Tools
- Sniffing Tools
- Sniffer Detection Techniques
- Promiscuous Detection Tools
![Hands On Experience skill]()
- Perform MAC Flooding, ARP Poisoning, MITM and DHCP Starvation Attack
- Spoof a MAC Address of a Linux Machine
- Perform Network Sniffing using Various Sniffing Tools
- Detect ARP Poisoning in a Switch-Based Network
![skill you will learn skill]()
- Packet Sniffing Techniques
- ARP and DNS Poisoning
- Sniffing Attack Methods
Social Engineering
Topics
- Social Engineering
- Types of Social Engineering
- Human-based Social Engineering Techniques
- Impersonation
- Computer-based Social Engineering Techniques
- Phishing & its Tools
- Perform Impersonation using Al
- Identity Theft
- Mobile-based Social Engineering Techniques
- Social Engineering Countermeasures
- Anti-Phishing Toolbar
![Hands On Experience skill]()
- Perform Social Engineering using Various Techniques
- Detect a Phishing Attack
- Social Engineering using Al
![skill you will learn skill]()
- Social Engineering Attacks
- Identity Theft Detection
- Audit Human-level Vulnerabilities
- Social Engineering Countermeasures
Denial-of-Service
Topics
- DoS Attack
- DDoS Attack
- Botnets
- DoS/DDoS Attack Techniques
- DoS/DDoS Attack Toolkits
- DoS/DDoS Attack Detection Techniques
- DoS/DDoS Protection Tools
- DoS/DDoS Protection Services
![Hands On Experience skill]()
- Perform a DoS and DDoS attack on a Target Host
- Detect and Protect Against DoS and DDoS Attacks
![skill you will learn skill]()
- DoD and DDoS Attacks
- DoS/DDoS Auditing Tools
- Attack Prevention Techniques
- DoS Countermeasures
Session Hijacking
Topics
- Session Hijacking
- Application-Level Session Hijacking
- Compromising Session IDs
- Session Hijacking
- Network-Level Session Hijacking
- TCP/IP Hijacking
- RST Hijacking
- Blind Hijacking
- Session Hijacking Tools
- Session Hijacking Detection Methods
- Session Hijacking Detection Tools
- Approaches to Prevent Session Hijacking
![Hands On Experience skill]()
- Perform Session Hijacking using various Tools
- Detect Session Hijacking
![skill you will learn skill]()
- Session Hijacking Techniques
- Session Hijacking Countermeasures
Evading IDS, Firewalls, and Honeypots
Topics
- Intrusion Detection System (IDS)
- Intrusion Prevention System (IPS)
- Firewall
- Types of Firewalls
- Intrusion Detection Tools
- Intrusion Prevention Tools
- IDS/Firewall Evasion Techniques
- NAC and Endpoint Security Evasion Techniques
- IDS/Firewall Evading Tools
- Honeypot
- Types of Honeypots
- Honeypot Tools
- IDS/Firewall Evasion Countermeasures
![Hands On Experience skill]()
- Perform Intrusion Detection using Various Tools
- Deploy Honeypot to Detect Malicious Network Traffic
- Bypass Firewall Rules using Tunneling
- Bypass Antivirus
![skill you will learn skill]()
- Firewall Evasion Techniques
- IDS bypass methods
- Honeypot Detection & Evasion
- Network Perimeter Auditing
Hacking Web Servers
Topics
- Web Server Architecture
- Web Server Vulnerabilities
- Web Server Attack
- DNS Server Hijacking
- Web Cache Poisoning Attack
- Web Server Footprinting/Banner Grabbing
- Directory Brute Forcing
- Vulnerability Scanning
- Web Server Password Hacking
- Web Server Attack Tools
- Web Server Attack Countermeasures
- Detecting Web Server Hacking Attempts
- Web Server Security Tools
![Hands On Experience skill]()
- Perform Web Server Reconnaissance using Various Tools
- Enumerate Web Server Information
- Perform a Web Server Attack
- Perform a Web Server Hacking using Al
![skill you will learn skill]()
- Web Server Attacks
- Web Server Reconnaissance
- Web Server Hacking using Al
- Web Server Security Countermeasures
Hacking Web Applications
Topics
- Web Application
- OWASP Top 10 Application Security Risks - 2021
- Web Application Attacks
- Footprint Web Infrastructure
- Analyze Web Applications
- Bypass Client-side Controls
- Attack Access Controls
- Attack Web Services
- Web API
- Webhooks
- Web API Hacking Methodology
- API Security Risks and Solutions
- Web Application Security Testing
- Web Application Fuzz Testing
- Encoding Schemes
- Web Application Attack Countermeasures
- Web Application Security Testing Tools
![Hands On Experience skill]()
- Perform Web Application Reconnaissance using Various Tools
- Perform Web Spidering
- Perform Web Application Vulnerability Scanning
- Perform Web Application Attacks
- Detect Web Application Vulnerabilities using Various Web Application Security Tools
- Perform Web Application Hacking using Al
![skill you will learn skill]()
- Web Application Attacks
- Web Application Hacking using Al
- Web Application Attack Countermeasures
SQL Injection
Topics
- SQL Injection
- Types of SQL Injection
- Error Based SQL Injection
- Union SQL Injection
- Blind/Inferential SQL Injection
- SQL Injection Methodology
- Information Gathering and SQL Injection Vulnerability Detection
- Launch SQL Injection Attacks
- Advanced SQL Injection
- SQL Injection Tools
- SQL Injection with Al
- Evasion Techniques
- SQL Injection Countermeasures
- SQL Injection Detection Tools
![Hands On Experience skill]()
- Perform an SQL Injection Attack Against MSSQL to Extract Databases
- Detect SQL Injection Vulnerabilities using Various SQL Injection Detection Tools
- Perform SQL Injection using Al
![skill you will learn skill]()
- SQL Injection Techniques
- SQL Injection Evasion
- SQL Injection Countermeasures
Hacking Wireless Networks
Topics
- Wireless Networks
- Wireless Standards
- Wireless Encryption
- Wireless Threats
- Wireless Hacking Methodology
- Wi-Fi Discovery
- Wireless Traffic Analysis
- Launch of Wireless Attacks
- Wi-Fi Encryption Cracking
- Wireless Attack Countermeasures
- Wi-Fi Security Auditing Tools
![Hands On Experience skill]()
- Footprint a Wireless Network
- Perform Wireless Traffic Analysis
- Crack a WPA2 Network
- Create a Rogue Access Point
![skill you will learn skill]()
- Wireless Network Security
- Wireless Network Hacking Methodology
- Wireless Security Testing tools
- Wireless Hacking Countermeasures
Hacking Mobile Platforms
Topics
- OWASP Top 10 Mobile Risks - 2024
- Anatomy of a Mobile Attack
- App Sandboxing Issues
- SMS Phishing Attack (SMiShing)
- Call Spoofing
- OTP Hijacking/Two-Factor Authentication Hijacking
- Camera/Microphone Capture Attacks
- Android Rooting
- Hacking Android Devices
- Android Hacking Tools
- Android Security Tools
- Jailbreaking iOS
- Hacking iOS Devices
- iOS Device Security Tools
- Mobile Device Management (MDM)
- OWASP Top 10 Mobile Risks and Solutions
- Mobile Security Guidelines
- Mobile Security Tools
![Hands On Experience skill]()
- Hack an Android Device by Creating Binary Payloads
- Exploit the Android Platform through ADB
- Hack an Android Device by Creating APK File
- Secure Android Devices using Various Android Security Tools
![skill you will learn skill]()
- Mobile Attack Vectors
- Android and iOS Hacking
- Mobile Device Management
- Mobile Security Tools
IoT and OT Hacking
Topics
- IoT Architecture
- IoT Technologies and Protocols
- OWASP Top 10 IoT Threats
- loT Vulnerabilities
- lot Threats
- loT Attacks
- IoT Hacking Methodology
- loT Hacking Tools
- IoT Security Tools
- IT/OT Convergence (IIOT)
- OT Technologies and Protocols
- OT Vulnerabilities
- OT Threats
- OT Attacks
- OT Hacking Methodology
- OT Hacking Tools
- OT Security Tools
![Hands On Experience skill]()
- Gather Information using Online Footprinting Tools
- Capture and Analyze loT Device Traffic
- Perform lot Attacks
![skill you will learn skill]()
- IoT Security and Technologies
- IoT Hacking countermeasures
Cloud Computing
Topics
- Cloud Computing
- Fog Computing
- Edge Computing
- Container
- Docker
- Kubernetes
- Serverless Computing
- OWASP Top 10 Cloud Security Risks
- Cloud Computing Threats
- Container Vulnerabilities
- Kubernetes Vulnerabilities
- Cloud Attacks
- Cloud Hacking Methodology
- AWS Hacking
- Microsoft Azure Hacking
- Google Cloud Hacking
- Container Hacking
- Cloud Network Security
- Cloud Security Controls
- Cloud Security Tools
![Hands On Experience skill]()
- Perform $3 Bucket Enumeration using Various $3 Bucket Enumeration Tools
- Exploit Open S3 Buckets
- Escalate IAM User Privileges by Exploiting Misconfigured User Policy
- Perform vulnerability assessment on docker images
![skill you will learn skill]()
- Cloud Computing Threats & Attacks
- Container & Serverless Security
- Cloud Hacking Methodologies
- Cloud Security Tools & Techniques
Cryptography
Topics
- Cryptography
- Ciphers
- Symmetric Encryption Algorithms
- Asymmetric Encryption Algorithms
- Quantum Cryptography
- Cryptography Tools
- Public Key Infrastructure (PKI)
- Signed Certificate
- Digital Signature
- Email Encryption
- Disk Encryption
- Blockchain
- Cryptanalysis Methods
- Cryptography Attacks
- Attacks on Blockchain
- Quantum Computing Attacks
- Cryptanalysis Tools
![Hands On Experience skill]()
- Encrypt the Information using Various Cryptography Tools
- Create and Use Self-signed Certificates
- Perform Email and Disk Encryption
- Perform Cryptanalysis using Various Cryptanalysis Tools
- Perform Cryptography using Al
![skill you will learn skill]()
- Encryption Algorithms
- Email and Disk Encryption
- Public Key Infrastructure (PKI)
- Cryptanalysis Tools
Free Career Counselling
We are happy to help you 24/7
Ethical Hacking Course in Mumbai Description
What are the key features of this CEH Certification Course in Mumbai?
- Participants from Mumbai get 6 months of complimentary access to the CEH v12 Hands-On Labs, enhancing practical learning experiences.
- The course kit, tailored for Mumbai professionals, comes equipped with comprehensive eCourseware from the EC-Council.
- Instructors are CEI Certified Trainers, offering Mumbai participants expert guidance and insights.
What are the prerequisites for this Ethical Hacking Course?
How do I become CEH Certified?
What will you learn as part of this CEH certification training course?
What are the objectives of this CEH certification course?
What does the CEH course cover?
the CEH program and accompanying exam cover an extensive range of topics crucial for those aspiring to become tactical cybersecurity professionals. The curriculum is designed to provide a thorough understanding of the kill-chain process, encompassing stages from footprinting and reconnaissance to scanning, gaining, and maintaining access, as well as techniques for concealing digital tracks. This detailed five-phase approach to ethical hacking is relevant for a variety of network and system environments, including traditional, cloud, hybrid, and IoT systems. Mumbai's participants will also learn about diverse tools and techniques used in these processes and how hackers employ similar tactics to breach organizations.
Is CEH a hands-on program?
What does a CEH do?
Who is a Certified Ethical Hacker (CEH)?
What makes this Ethical Hacking course different from others in the market?
How will I execute the practicals in this CEH course in Mumbai?
How much programming coding skills are required for this CEH certification training program?
What are the system requirements for this CEH course?
- Memory – Minimum 4 GB RAM
- Processor – Intel Core i3 CPU @2.00 GHz or later
- Storage – 250 GB HDD/SDD or later
CEH Exam and Certificate in Mumbai
To get CEH certified, you can either complete official training through EC-Council-approved providers or apply based on relevant work experience. Once approved, you can take the exam at a training center, online via remote proctoring, or at a Pearson VUE center.
EC-Council does not publish official pass rates, but global averages range from 60% to 85%. The CEH exam is ANAB-accredited and designed to be fair for candidates with varying experience levels. Official training and preparation materials are available to help candidates succeed.
Yes, candidates who wish to bypass the official training and jump straight to the exam may apply for eligibility. If granted, you can take the examination directly.
reviews
Read learner testimonials
Hear from our learners
Ethical Hacking Training in Mumbai FAQs
Is Ethical Hacking a good career?
A CEH certified professional is trusted by various Fortune 500 companies such as IBM,
Microsoft, Cisco, and many more. As per, U.S. BUREAU OF LABOR STATISTICS, 2022, Employment of information security analysts is projected to grow 33 percent from 2020 to 2030, much faster than the average for all occupations. Since the demand is high, Ethical Hacking is one of the most sought after and promising professions at the moment.
Is CEH a good certification?
Who are the instructors at Edureka for the Ethical Hacking Course in Mumbai?
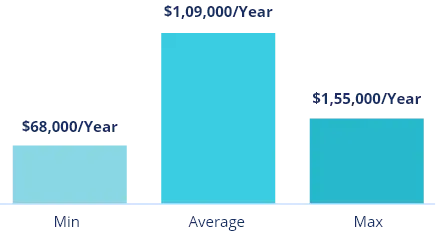
What is the average salary of a Certified Ethical Hacker in Mumbai?
Is this live training, or will I watch pre-recorded videos?
Which top companies hire certified ethical hackers?
Can I review my answers during the CEH examination?
Can a beginner learn ethical hacking?
What if I miss a class?
Can I take the CEH certification exam online?
Where can I find the most effective Ethical Hacking certification training near me in Mumbai?
What are the job roles available after getting a CEH certification in Mumbai?
- System Security Administrator
- Security Analyst
- Information Security Manager
- Cyber Security Consultant
- IT Security Administrator
- Network Engineer
- Vulnerability Assessment Analyst
- Penetration Tester
What is the salary if a person has Ethical hacking certification?
What is the duration of the CEH Exam?
What is the EC-Council CEH v12 Certification exam pattern?
Test Duration: 4 Hours
Test Format: Multiple Choice
Test Delivery: ECC EXAM, VUE
Exam Prefix: 312-50 (ECC EXAM), 312-50 (VUE)
Passing Score: 70%
Does hacking require coding?
What is the future scope after becoming a certified ethical hacker?
- CISSP Certification
- CISA Certification
- CISM Certification
- OSCP Certification
What necessary tools are required to attend the Ethical Hacking training sessions?
- For Windows it is required to have atleast Windows XP SP3 or higher.
- For Mac you must have OSX 10.6 or higher.
- Good Internet speed.
- Headset, microphone, and speakers.
How long is the CEH certification valid?
Can I do CEH after 12th?
Can a beginner learn ethical hacking?
How do I enroll in the online Ethical Hacking training in Mumbai?
- American Express
- Visa Credit or Debit Card
- PayPal
- MasterCard
- Diner’s Club
How does CEH v12 differ from CEH v11?
What are the different job roles for certified ethical hackers?
Do hackers make use of Python programming?
Will CEH Certification get me a job?
What skills should an Ethical Hacker Possess?
How much are the ethical hacking course fees?
What book do you suggest reading for Ethical Hacking?
Book Title: Hacking - A Beginners Guide to Computer Hacking, basic Security and Penetration testing.
Author : John Slavio
Book Title: Penetration Testing - A Hands On Introduction to Hacking
Author : Georgia Weidman
Book Title : Hacking - The Art of Exploitation.
Author : Jon Erickson

