Cyber Security and Ethical Hacking Internship ...
- 15k Enrolled Learners
- Weekend/Weekday
- Live Class
Enumeration serves as a vital technique in ethical hacking, essential for pinpointing system vulnerabilities and potential entry points. Mastery of enumeration in ethical hacking is indispensable for every ethical hacker to strengthen an organisation’s security stance effectively.
Table of Contents

Enumeration refers to the process of extracting information relevant to a target system or network. This process requires ethical hackers to thoroughly probe and analyse systems to retrieve crucial system-related information. This includes usernames, web server details, operating system details, and other infrastructure-related information that could assist in identifying potential vulnerabilities.
Enumeration not only forms its foundation but also provides critical grounding for subsequent steps, including vulnerability assessment and penetration testing.
Enumeration plays a key role in strengthening cyber security. It provides ethical hackers with detailed insight into the functioning of devices on your network. This includes their location and the type of information being transmitted or received.
In simple terms, the enumeration process collects the details of your system network to assess open ports on your system, the ones accessing specific information, and, if they do, what kind of information is being transferred. This information enables hackers to run pre-emptive tests using manual and automated tools, and, as a result, find security gaps before they translate into real-world attacks.
Moreover, enumeration facilitates the construction of a thorough inventory of an organisation’s IT assets. This, in turn, improves risk management and ensures compliance with industry standards.
Also Read : Understanding of Privilege Escalations
During the enumeration process, various types of sensitive information can be exposed. Some of the common targets include:
Now, let’s understand what is enumeration in hacking and how it is carried out.
Related Post : Reconnaissance in Ethical Hacking
Active scanning and passive scanning typically form the two main approaches of enumeration in ethical hacking, a crucial step in ethical hacking. This process yields valuable insights into potential entry points and vulnerabilities within the target system. We will now explore each approach extensively, considering the unique characteristics and techniques involved.
Actively scanning is a proactive approach that directly interacts with the target system to gather information. This method, more aggressive than passive scanning, probes the system actively, finding vulnerabilities and collecting data. Techniques employed in active scanning encompass several key methods, notably:
This involves the active process of dispatching packets to distinct target system ports. Through this, we discern their operational status—open, closed, or filtered. By identifying running services and potential entry points with precision, this technique proves invaluable in enhancing system security. Commonly employed tools for port scanning include Nmap and Unicornscan.
Beyond mere port scanning, it engages in active interaction with identified services to amass a wealth of detailed information. This includes ascertaining service versions, configurations, and even potential vulnerabilities. For this purpose, specialists utilise tools such as Nmap, leveraging its version scanning option, and Amap for rigorous service probing.
In vulnerability scanning, we employ automated tools to pinpoint recognised vulnerabilities within the target system. These instruments juxtapose the system’s configuration and software versions with a database of acknowledged weaknesses, thus presenting a potential security gap report. Some well-regarded vulnerability scan utilities are Nessus, OpenVAS, and Nexpose.
Although active scanning provides thorough results and reveals vulnerabilities, it has its own share of drawbacks. It creates network traffic, making it detectable by Intrusion Detection Systems (IDS) or firewalls. Furthermore, this method can trigger alarms, potentially compromising ethical hackers’ activities.
On the other hand, passive scanning adopts a more subtle approach to enumeration. It hinges on the observation of network traffic and analysis of publicly available information, avoiding direct interaction with the target system. Techniques involved in passive scanning encompass:
Packet sniffing comprises the practice of capturing and analysing network traffic to gather information about the target system. By monitoring this traffic, ethical hacking can discern communication patterns, identify protocols in use, and potentially detect sensitive data being transmitted. Tools such as Wireshark and tcpdump are prevalent for packet sniffing.
Open Source Intelligence (OSINT) denotes the methodical collection and analysis of publicly available information about a target organisation or system. It encompasses an in-depth exploration of various online resources, such as the company’s website, social media presence, and job postings, among others. Through this process, valuable insights are unveiled concerning aspects like organisational structure and utilised technologies within the entity under scrutiny.
It involves the gathering of information through direct human interaction, specifically phishing emails, phone calls, or even physical impersonation. Ethical hackers manipulate individuals into revealing sensitive data; hence, they gain a profound understanding of not only the target system’s security posture but also its potential weaknesses.
The advantage of passive scanning lies in its stealthiness and reduced detectability by security mechanisms. It enables ethical hackers to amass information without triggering any alerts for the administrators of the target system.
Nonetheless, compared with active scanning, which actively probes for vulnerabilities, passive methods might yield limited results. If you’re hoping to get a better grasp of these concepts of enumeration types, EC-Council’s expansive catalogue can offer you deeper insights into this.
When performing enumeration, ethical hackers should consider the following best practices:
Let’s now look at some of the techniques that ethical hackers employ to effectively perform enumeration:
Mastering these techniques is essential for conducting thorough enumeration and identifying potential vulnerabilities.
If you find these concepts and ideas intriguing at this stage, consider delving into our comprehensive ethical hacking tutorial to enrich your knowledge further. Equipped with appropriate training–not to mention a proper mindset–you can launch an enriching career in ethical hacking, one that contributes significantly towards combating cyber threats.
Related Post : Ethical Issues in Information Technology
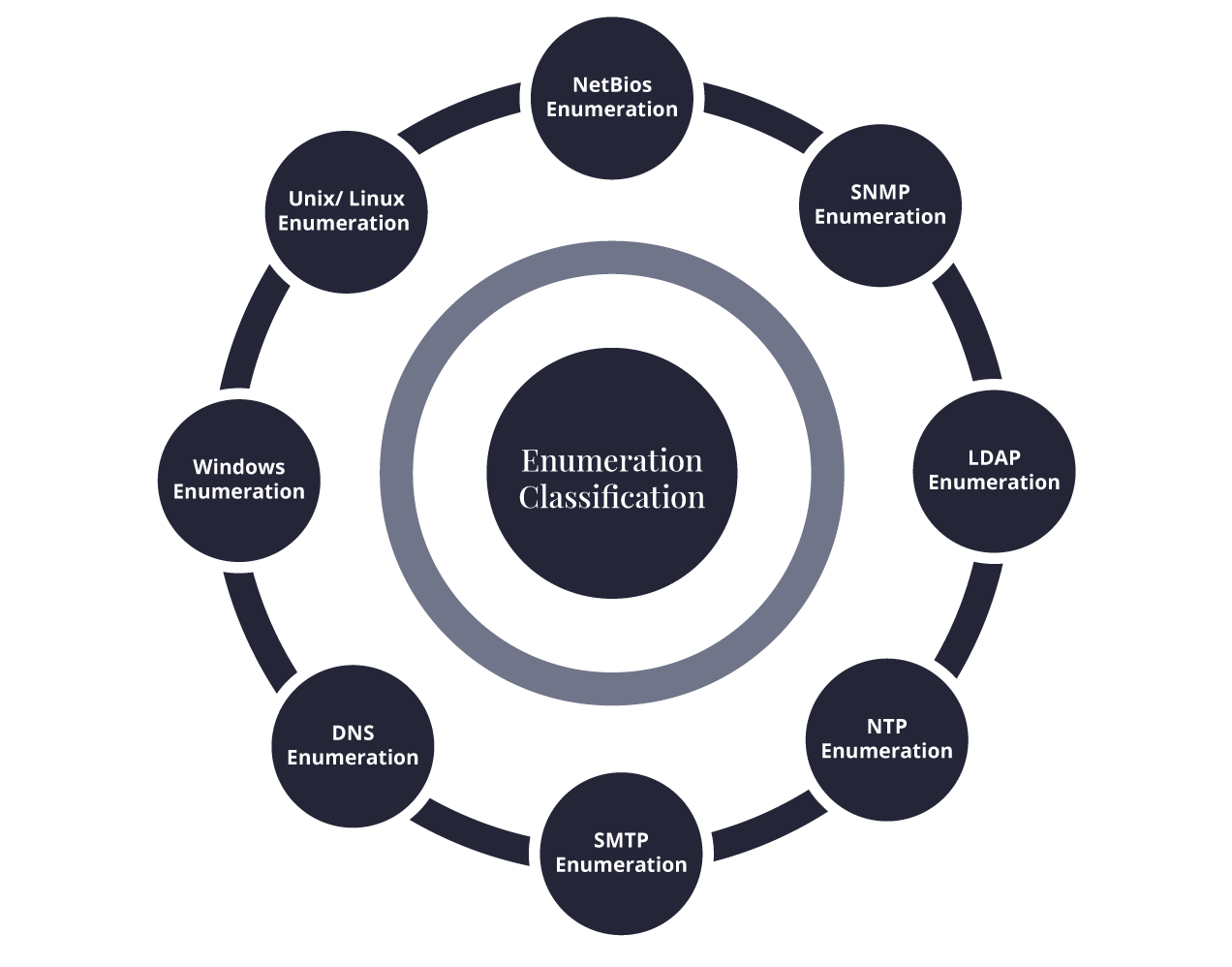
Let’s delve into a few common types of enumeration based on the specific protocols and services it targets:
The focus of NetBIOS enumeration lies in the accumulation of data from Windows systems that utilise the NetBIOS protocol. This process has the potential to disclose various details, including hostnames, shared resources, and user sessions. Commonly employed tools for executing a successful NetBIOS enumeration are Nbtstat and Nbtscan.
Ethical hackers target devices with Simple Network Management Protocol (SNMP) enabled for SNMP enumeration. They can retrieve system information, network configurations, and even sensitive data such as usernames and passwords by querying SNMP servers. Popular tools used in this process include SNMPwalk and Onesixtyone.
LDAP enumeration involves querying Lightweight Directory Access Protocol (LDAP) servers to gather information regarding users, groups, and organisational structure. Ethical hackers utilise tools like LDAPSearch to extract valuable data from these directories.
Ethical hackers actively pursue Network Time Protocol (NTP) enumeration to collect information from NTP servers. Through strategic querying of these servers, they gain access to the system’s time configuration details. This knowledge proves beneficial in two ways: first, it aids them in plotting time-based attacks, and second, it enables the identification of misconfigured systems.
Various services and ports commonly found in network environments can undergo the application of enumeration techniques. The key services and ports typically targeted during this process include:
Ethical hackers, by concentrating on these specific services and ports, can unveil an abundance of information in the enumeration process.
An ethical hacker leverages enumeration as a fundamental skill. Proficiency in its techniques and recognising its critical significance aids in effectively identifying system vulnerabilities. This proactive approach strengthens an organisation’s security stance; hence, comprehending and implementing thorough enumerative methods is not merely advised but essential.
Whether you’re preparing for CEH certification or looking to become an ethical hacker, gaining expertise in enumeration is crucial for a successful career in ethical hacking. Join Edureka today for a rewarding career in cybersecurity and ethical hacking!
 Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUPedureka.co